We’ve previously reported from the UK about the Online Safety Bill, a piece of internet safety legislation that contains several concerning provisions relating to online privacy and encryption. UK laws enter the statutes by royal assent after being approved by Parliament, so with the signature of the King, it has now become the law of the land as the Online Safety Act 2023. Now that it’s beyond amendment, it’s time to take stock for a minute: what does it mean for internet users, both in the UK and beyond its shores? Continue reading “The UK Online Safety Bill Becomes Law, What Does It Mean?”
privacy91 Articles
Your Car Is A Privacy Nightmare On Wheels
There was a time when a car was a machine, one which only came to life when its key was turned, and functioned simply as a way to get its occupants from point A to B. For most consumers that remains the case, but unfortunately in the last decade its function has changed from the point of view of a car manufacturer. Motor vehicles have become a software product as much as a hardware one, and your car now comes with all the privacy hazards you’d expect from a mobile phone or a computer. The Mozilla Foundation have taken a look at this problem, and their disturbing finding was that every one of the 25 major automotive brands they tested had significant failings.
Their quote that the cars can collect “deeply personal data such as sexual activity, immigration status, race, facial expressions, weight, health and genetic information, and where you drive.” had us wondering just exactly what kind of sensors they incorporate in today’s vehicles. But beyond mild amusement at some of the possibilities, it’s clear that a car manufacturer can glean a significant amount of information and has begun doing so largely without the awareness of the consumer.
We’ve railed about unnecessary over-computerisation of cars in the past, but from an obsolescence and reliability perspective rather than a privacy one, so it’s clear that the two issues are interconnected. There needs to be some level of public awareness that cars can do this to their owners, and while such things as this Mozilla investigation are great, the message needs to appear in more consumer-focused media.
As well as the summary, Mozilla also provide a detailed report broken down by carmaker.
Header: Michael Sheehan, CC BY 2.0.
Smart Doorbell Focuses On Privacy
As handy as having a smart doorbell is, with its ability to remotely see who’s at the front door from anywhere with an Internet connection, the off-the-shelf units are not typically known for keeping user privacy as a top priority. Even if their cloud storage systems were perfectly secure (which is not a wise assumption to make) they have been known to give governmental agencies and police free reign to view the videos whenever they like. Unfortunately if you take privacy seriously, you might need to implement your own smart doorbell yourself.
The project uses an ESP32-CAM board as the doorbell’s core, paired with a momentary push button and all housed inside a 3D-printed enclosure. [Tristam] provides a step-by-step guide, including printing the enclosure, configuring the ESP32-CAM to work with the popular open-source home automation system ESPHome, handling doorbell notifications automatically, and wiring the components. There are plenty of other optional components that can be added to this system as well, including things like LED lighting for better nighttime imaging.
[Tristam] isn’t much of a fan of having his home automation connected to the Internet, so the device eschews wireless connections and batteries in favor of a ten-meter USB cable connected to it from a remote machine. As far as privacy goes, this is probably the best of all worlds as long as your home network isn’t doing anything crazy like exposing ports to the broader Internet. It also doesn’t need to be set up to continuously stream video either; this implementation only takes a snapshot when the doorbell button is actually pressed. Of course, with a few upgrades to the ESP circuitry it is certainly possible to use these chips to capture video if you prefer.
Thanks to [JohnU] for the tip!
The British Government Is Coming For Your Privacy
The list of bad legislation relating to the topic of encryption and privacy is long and inglorious. Usually, these legislative stinkers only affect those unfortunate enough to live in the country that passed them. Still, one upcoming law from the British government should have us all concerned. The Online Safety Bill started as the usual think-of-the-children stuff, but as the EFF notes, some of its proposed powers have the potential to undermine encryption worldwide.
At issue is the proposal that services with strong encryption incorporate government-sanctioned backdoors to give the spooks free rein to snoop on communications. We imagine that this will be of significant interest to some of the world’s less savoury regimes, a club we can’t honestly say the current UK government doesn’t seem hell-bent on joining. The Bill has had a tumultuous passage through the Lords, the UK upper house, but PM Rishi Sunak’s administration has proved unbending.
If there’s a silver lining to this legislative train wreck, it’s that many of the global tech companies are likely to pull their products from the UK market rather than comply. We understand that UK lawmakers are partial to encrypted online messaging platforms. Thus, there will be poetic justice in their voting once more for a disastrous bill with the unintended consequence of taking away something they rely on.
Header image: DaniKauf, CC BY-SA 3.0.
Disabling Intel’s Backdoors On Modern Laptops
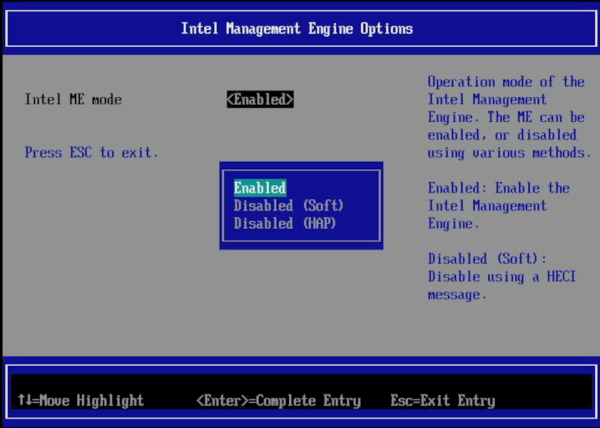
Despite some companies making strides with ARM, for the most part, the desktop and laptop space is still dominated by x86 machines. For all their advantages, they have a glaring flaw for anyone concerned with privacy or security in the form of a hardware backdoor that can access virtually any part of the computer even with the power off. AMD calls their system the Platform Security Processor (PSP) and Intel’s is known as the Intel Management Engine (IME).
To fully disable these co-processors a computer from before 2008 is required, but if you need more modern hardware than that which still respects your privacy and security concerns you’ll need to either buy an ARM device, or disable the IME like NovaCustom has managed to do with their NS51 series laptop.
NovaCustom specializes in building custom laptops with customizations for various components and specifications to fit their needs, including options for the CPU, GPU, RAM, storage, keyboard layout, and other considerations. They favor Coreboot as a bootloader which already goes a long way to eliminating proprietary closed-source software at a fundamental level, but not all Coreboot machines have the IME completely disabled. There are two ways to do this, the HECI method which is better than nothing but not fully trusted, and the HAP bit, which completely disables the IME. NovaCustom is using the HAP bit approach to disable the IME, meaning that although it’s not completely eliminated from the computer, it is turned off in a way that’s at least good enough for computers that the NSA uses.
There are a lot of new computer manufacturers building conscientious hardware nowadays, but (with the notable exception of System76) the IME and PSP seem to be largely ignored by most computing companies we’d otherwise expect to care about an option like this. It’s certainly still an area of concern considering how much power the IME and PSP are given over their host computers, and we have seen even mainline manufacturers sometimes offer systems with the IME disabled. The only other options to solve this problem are based around specific motherboards for 8th and 9th generation Intel desktops, or you can go way back to hardware from 2008 and install libreboot to eliminate, rather than disable, the IME.
Thanks to [Maik] for the tip!
Hackaday Links: August 28, 2022
The countdown for the first step on humanity’s return to the Moon has begun. The countdown for Artemis 1 started on Saturday morning, and if all goes well, the un-crewed Orion spacecraft atop the giant Space Launch Systems (SLS) booster will liftoff from the storied Pad 39B at Cape Canaveral on Monday, August 29, at 8:33 AM EDT (1233 GMT). The mission is slated to last for about 42 days, which seems longish considering the longest manned Apollo missions only lasted around 12 days. But, without the constraint of storing enough consumables for a crew, Artemis is free to take the scenic route to the Moon, as it were. No matter what your position is on manned space exploration, it’s hard to deny that launching a rocket as big as the SLS is something to get excited about. After all, it’s been 50 years since anything remotely as powerful as the SLS has headed to space, and it’s an event that’s expected to draw 100,000 people to watch it in person. We’ll have to stick to the NASA live stream ourselves; having seen a Space Shuttle launch in person in 1990, we can’t express how much we envy anyone who gets to experience this launch up close.
Continue reading “Hackaday Links: August 28, 2022”
You Break It, We Fix It
Apple’s AirTags have caused a stir, but for all the wrong reasons. First, they turn all iPhones into Bluetooth LE beacon repeaters, without the owner’s permission. The phones listen for the AirTags, encrypt their location, and send the data on to the iCloud, where the tag’s owner can decrypt the location and track it down. Bad people have figured out that this lets them track their targets without their knowledge, turning all iPhone users into potential accomplices to stalkings, or worse.
Naturally, Apple has tried to respond by implementing some privacy-protecting features. But they’re imperfect to the point of being almost useless. For instance, AirTags now beep once they’ve been out of range of their owner’s phone for a while, which would surely alert the target that they’re being tracked, right? Well, unless the evil-doer took the speaker out, or bought one with the speaker already removed — and there’s a surprising market for these online.
 If you want to know that you’re being traced, Apple “innovated with the first-ever proactive system to alert you of unwanted tracking”, which almost helped patch up the problem they created, but it only runs on Apple phones. It’s not clear what they meant by “first-ever” because hackers and researchers from the SeeMoo group at the Technical University of Darmstadt beat them to it by at least four months with the open-source AirGuard project that runs on the other 75% of phones out there.
If you want to know that you’re being traced, Apple “innovated with the first-ever proactive system to alert you of unwanted tracking”, which almost helped patch up the problem they created, but it only runs on Apple phones. It’s not clear what they meant by “first-ever” because hackers and researchers from the SeeMoo group at the Technical University of Darmstadt beat them to it by at least four months with the open-source AirGuard project that runs on the other 75% of phones out there.
Along the way, the SeeMoo group also reverse engineered the AirTag system, allowing anything that can send BLE beacons to play along. This opened the door for [Fabian Bräunlein]’s ID-hopping “Find You” attack that breaks all of the tracker-detectors by using an ESP32 instead of an AirTag. His basic point is that most of the privacy guarantees that Apple is trying to make on the “Find My” system rely on criminals using unmodified AirTags, and that’s not very likely.
To be fair, Apple can’t win here. They want to build a tracking network where only the good people do the tracking. But the device can’t tell if you’re looking for your misplaced keys or stalking a swimsuit model. It can’t tell if you’re silencing it because you don’t want it beeping around your dog’s neck while you’re away at work, or because you’ve planted it on a luxury car that you’d like to lift when its owners are away. There’s no technological solution for that fundamental problem.
But hackers are patching up the holes they can, and making the other holes visible, so that we can at least have a reasonable discussion about the tech’s tradeoffs. Apple seems content to have naively opened up a Pandora’s box of privacy violation. Somehow it’s up to us to figure out a way to close it.