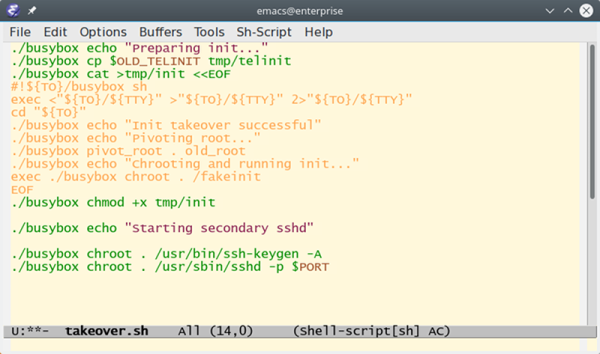
Did you know you can run remote Linux GUI programs in a browser with HTML5 support? It’s even secure because you can use SSH tunneling and that little trick means you don’t even need to open additional ports. If this sounds like gibberish, read on, it’s actually pretty easy to get up and running.
I recently was a guest on a Houston-based podcast, and the hosts asked me if the best thing about writing for Hackaday was getting to work with the other Hackaday staff. I told them that was really good, but what I like best was interacting with people (well, most people) in the comments. That sometimes you’d post an article and someone would bring a topic up in comments that would really knock your socks off. This is how I wound up with this nearly ideal remote access solution, that requires nothing on the remote side but a web browser.
A while back I posted about keeping programs running after log off on a Linux box. The post was mostly about non-GUI programs but you could use NX or VNC to handle it. In the comments, someone mentioned how unhappy they’d been with recent copies of NX and another commenter called [Screen for X11] posted about a tool called xpra.