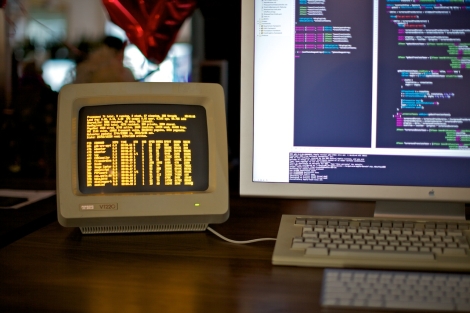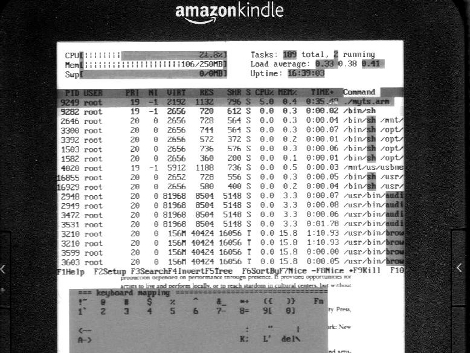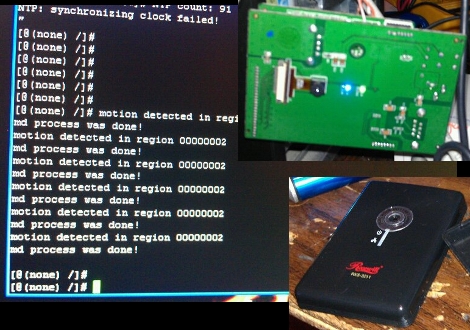
[Shawn] emailed us some pictures and a description of his latest hack. He cracked open a Rosewill RXS-3211 IP Camera because the output of the web interface made him certain that it was running Linux and he wanted to unlock some more potential from the device. These cameras are used for security, and offer a browser-based interface via a WiFi connection. After studying the circuit board he started poking around an unpopulated set of four pads and managed to get a serial connection up and running. The device’s serial terminal operates at 115200 baud using eight data bits, one stop bit, and even parity.
He wonder where to go from here and we have a few ideas. You can see in the terminal readout above that it announces when motion is detected. We think this motion detection would be quite useful with a small rover while adding live video broadcasting at the same time. An embedded Linux system should be able to interface with the device and we think that a bit of creative coding would open up the WiFi connection for other use as well. Not bad for a module that can be had for as little as $29. We’ve included all the images [Shawn] sent us after the break and we’d love to hear your thoughts on what you’d use this for in the comments.
Continue reading “I Am Root! – IP Camera Shell Access” →