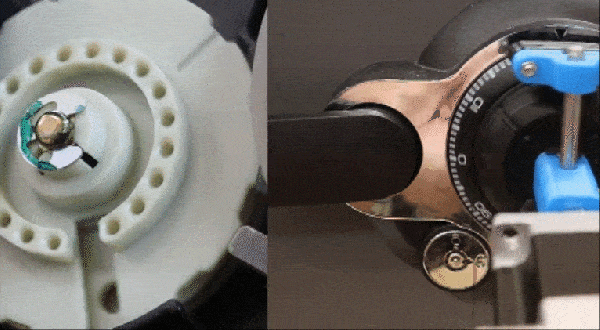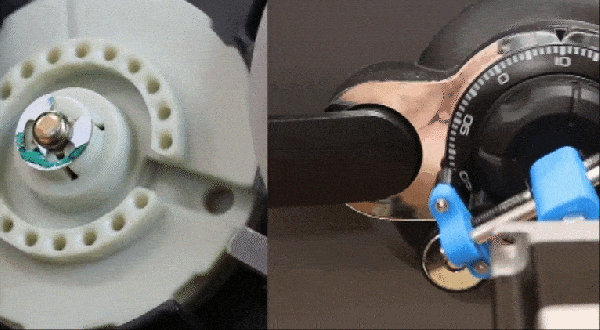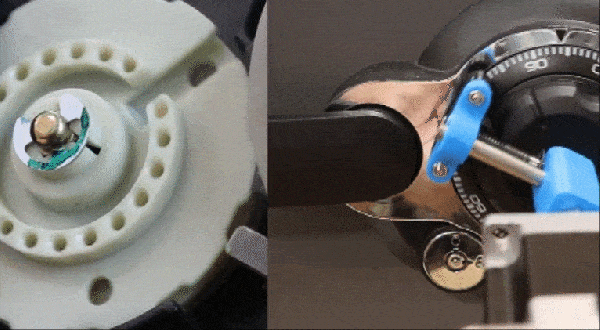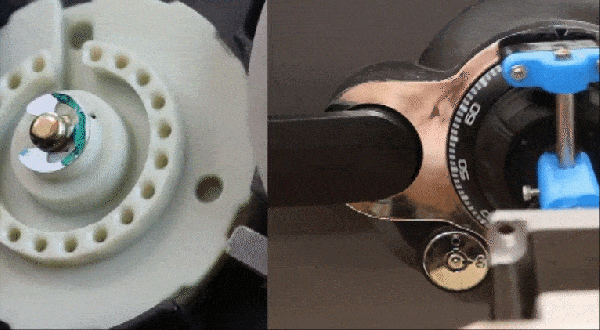
Physical security is often considered simpler than digital security since safes are heavy and physical keys take more effort to duplicate than those of the digital persuasion. [Maxime Beasse and Quentin Clement] have developed a smartphone app that can duplicate a key from a photo making key copying much easier.
KeyDecoder is an open source Android app that can generate all the necessary bitting info to duplicate a key from just an image. Luckily for the paranoid among us, the image must be taken with the key laying flat without a keyring on an ISO/CEI 7810 ID-1 ID or credit card. A passerby can’t just snap a photo of your keys across the room and go liberate your home furnishings, but it still would be wise to keep a closer eye on your keys now that this particular cat hack is out of the bag.
The project’s GitHub page is awash in warnings that this tool is designed solely for “pentesters and security enthusiasts” to warn their friends and clients about the dangers of leaving their keys exposed. After learning about this tool, we wouldn’t be surprised if some in the audience start rethinking how they carry and store their physical keys from now on.
If you want to see some more hacks to duplicate keys, checkout Copying High Security Keys With OpenSCAD And Light and Methods Of Copying High Security Keys.