One effect of the global pandemic was that there were relatively few events in our sphere for a couple of years. This and that other by-product of COVID-19, the chip shortage, meant that over the past year we’ve been treated to several event badges that should have appeared in 2020 or 2021, but didn’t due to those cancelled events. We were lucky enough to receive probably the last of these delayed badges in mid February, as we made the journey to the central part of the Netherlands to Hacker Hotel 2023.
A Puzzle, A 4-Bit Computer, And An Artwork
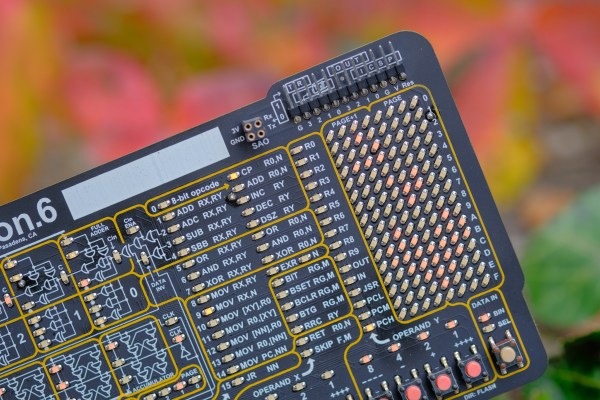
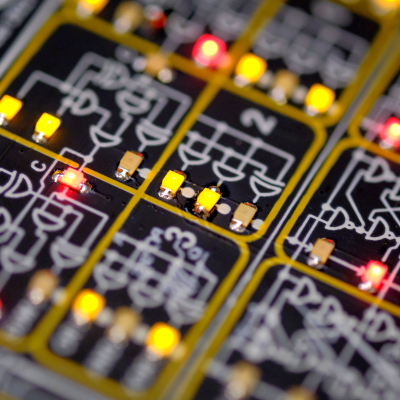
The badge takes the form of a rectangular PCB with all parts on the top side. The brains of the operation is an RP2040, and it’s powered by a CR2032 coin cell in a holder. It’s divided into two parts, the top third which carries the circuitry and the lower two thirds of which as a row of buttons and LEDs. It’s pretty obvious from the start that it has data and address lines of a 4-bit computer, and as well as these there is an evident serial port and a USB socket. The artwork comes form the same artist whose work graced both the previous Hacker Hotel badge and the MCH2022 badge, and the rear of the PCB makes full use of all layers to create a mystical puzzle. The sum is to create a puzzle game intended to entertain the visitor, take them round the venue, and find clues to an eventual solution. I love the design both from an artistic and technical viewpoint, but have to admit that the puzzle aspect isn’t really my thing. Thus here we’ll concentrate on the badge hardware and production, and mention the puzzles only in passing. Continue reading “Hacker Hotel 2023 Had A Very Cool Badge”


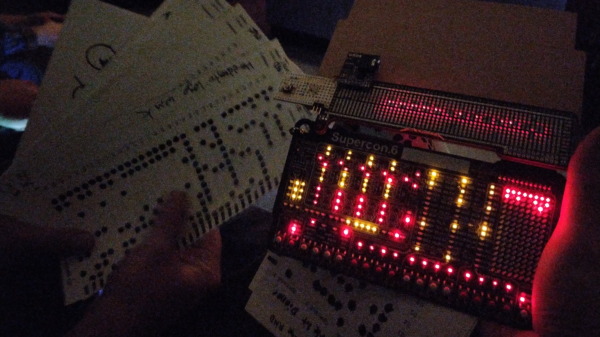
 usual facilities back home, [Ben] and [Zach] obviously had to improvise with whatever they had with them, and whatever could be scrounged off other badges or other hardware lying around.
usual facilities back home, [Ben] and [Zach] obviously had to improvise with whatever they had with them, and whatever could be scrounged off other badges or other hardware lying around.