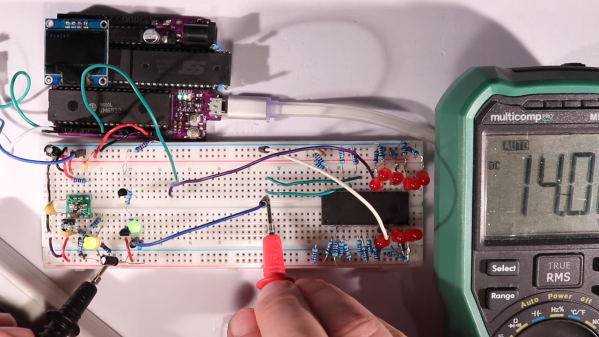
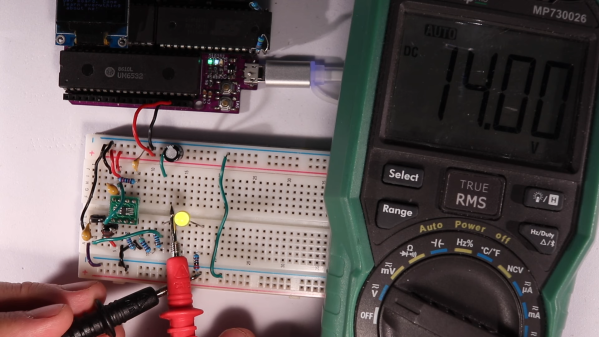
There’s treasures hidden in old technology, and you deserve to be able to revive it. Whether it’s old personal computer platforms, vending machines, robot arms, or educational kits based on retro platforms, you will need to work with parallel EEPROM chips at some point. [Anders Nielsen] was about to do just that, when he found out that a TL866, a commonly used programmer kit for such ROMs, would cost entire $70 – significantly raising the budget of any parallel ROM-involving hacking. After months of work, he is happy to bring us a project – the Relatively Universal ROM Programmer, an open-source parallel ROM programmer board that you can easily assemble or buy.
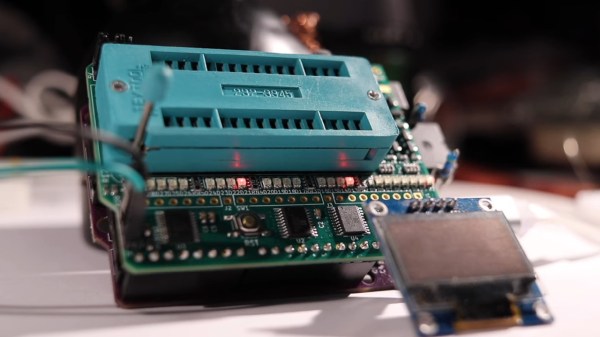
Designed in the Arduino shield format, there’s a lot of care and love put into making this board as universal as reasonably possible, so that it fits any of the old flash chips you might want to flash – whether it’s an old UV-erasable ROM that wants a voltage up to 30 V to be written, or the newer 5 V-friendly chips. You can use ICs with pin count from 24 to 32 pins, it’s straightforward to use a ZIF socket with this board, there’s LED indication and silkscreen markings so that you can see and tweak the programming process, and it’s masterfully optimized for automated assembly.
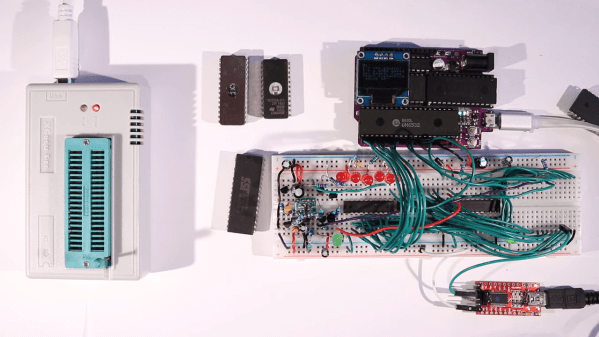
You can breadboard this programmer platform as we’ve previously covered, you can assemble our own boards using the open-source files, and if you don’t want to do either, you can buy the assembled boards from [Anders Nielsen] too! The software is currently work in progress, since that’s part of the secret sauce that makes the $70 programmers tick. You do need to adjust the programming voltage manually, but that can be later improved with a small hardware fix. In total, if you just want to program a few ROM chips, this board saves you a fair bit of money.
Continue reading “Relatively Universal ROM Programmer Makes Retro Tech Hacking Accessible”