Leaving your freezer door open accidentally is a great way to make a huge mess in the kitchen. [Guy Dupont] had a freezer that would regularly fail to close properly, and was sick of the regular meltdown events. Thus, he whipped up a very digital solution.
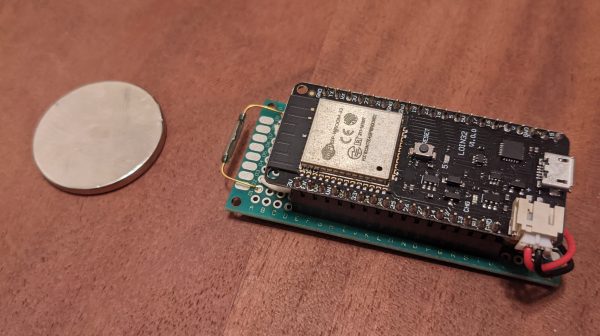
The build combines an ESP32 with a reed switch, which is activated by a magnet on the freezer door. If the freezer door is open, the reed switch similarly remains open. The ESP32 checks the switch status every few minutes, and if the door remains open for two consecutive checks, it raises the alarm. A notification is sent to [Guy] via WiFi so that he can rectify the situation. The rig runs off a 400 mAh battery, which lasts for just over three weeks running door checks at two minute intervals.
Based on [Guy]’s YouTube video, it appears the freezer door is jamming up against the wall. Perhaps shoving the freezer into a better position would help, though we suspect he would have thought of that first. And, in his own words, “That would be a very boring YouTube video, wouldn’t it?”
It’s not the first fridge alarm we’ve featured, and it won’t be the last, refrigeration gods willing.
Continue reading “ESP32 Freezer Alarm Keeps Tabs On Tricky Door”