I knew something had changed before I even paid for my ticket to this year’s Vintage Computer Festival East at the InfoAge Science and History Museum in Wall, New Jersey.
Over the last couple of years, attendance has been growing to the point that parking in the lot directly next to the main entrance has been reserved for only the earliest of risers. That hasn’t described yours truly since the days when I still had what my wife refers to as a “real job”, so that’s meant parking in the overflow lot down the road and walking the half a mile or so back to the main gate. Penance for working on the Internet, let’s call it.
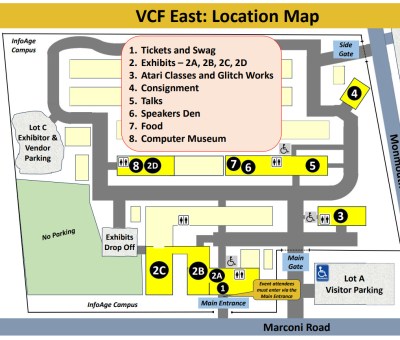 But this time, while walking along the fence that surrounds the sprawling InfoAge campus, I came across an open gate and a volunteer selling tickets. When commenting to her that this was a pleasant surprise compared to the march I’d anticipated, she responded that there had been so many people trying to get into the main entrance that morning that they decided to station her out here to handle the overflow.
But this time, while walking along the fence that surrounds the sprawling InfoAge campus, I came across an open gate and a volunteer selling tickets. When commenting to her that this was a pleasant surprise compared to the march I’d anticipated, she responded that there had been so many people trying to get into the main entrance that morning that they decided to station her out here to handle the overflow.
I was a few steps past her table and into InfoAge before the implications of this interaction really hit me. Two entrances. How many attendees does there need to be before you setup a secondary ticket booth out by the reserve parking lot just to keep things moving smoothly? Well, I can’t tell you what the exact number is. But after spending the rest of the day walking between all the buildings it took to contain all of the exhibits, talks, and activities this year, I can tell you it’s however many people came to VCF East 2024.
Compared to its relatively humble beginnings, it’s incredible to see what this event has grown into. InfoAge was packed to the rafters, and despite what you might think about a festival celebrating decades old computing hardware, there were plenty of young faces in the crowd. I’m not sure exactly what’s changed, but the whole place was positively jumping. Perhaps it’s partially the generational nostalgia that’s kept Netflix cranking out new seasons of the 1980’s set Stranger Things. I’m sure attention (and attendance) from several well known YouTube personalities have played a big part as well.
Whatever the magic formula that’s turned what was once a somewhat somber retrospective on early desktop computers into a major destination for tech lovers, I’m all for it. Love Live the Vintage Computer Festival!
Continue reading “VCF East 2024 Was Bigger And Better Than Ever” →