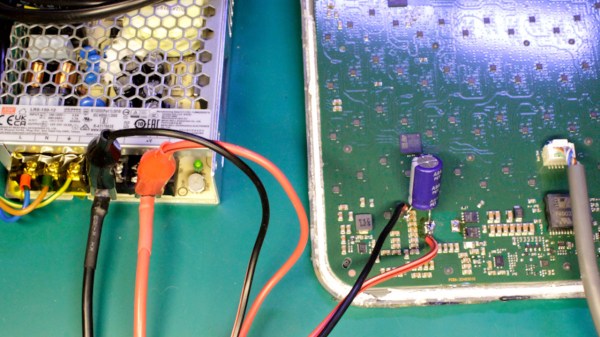
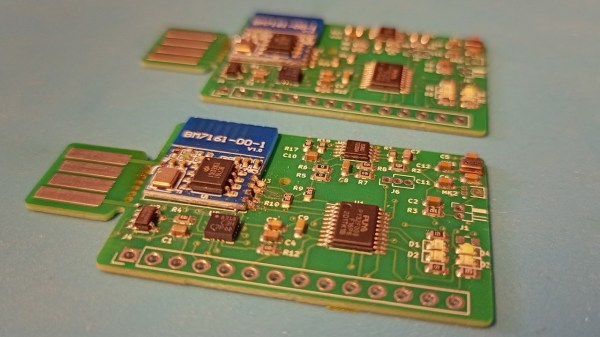
In our continuing coverage of the ROG Ally modding community, we would be amiss to not mention a seriously impressive mod — a dual screen project for the x86 gaming handheld by [YesItsKira]! Single screen devices can feel cramped, and this mod is a prime example of a dedicated hacker taking things into her own hands. In particular, the mechanics of this mod are done wonderfully, thanks to a custom-designed 3D printed Ally back cover.
 The second screen connects through a USB-C port, held above the main screen by a sturdy printed hinge at whatever angle you want it. As a pleasant surprise, it’s also touch-enabled! The mod is fully open source and well documented — everything you need to print is published on Thingiverse, a detailed assembly guide with pictures is on GitHub, and the BOM is at the bottom of the guide.
The second screen connects through a USB-C port, held above the main screen by a sturdy printed hinge at whatever angle you want it. As a pleasant surprise, it’s also touch-enabled! The mod is fully open source and well documented — everything you need to print is published on Thingiverse, a detailed assembly guide with pictures is on GitHub, and the BOM is at the bottom of the guide.
Apart from printed parts, you only need a few things off Amazon, it’s that easy to source. Electronics-wise, this mod uses a Raspberry Pi-suited HDMI screen, wiring it up through an integrated USB-C dock; which means you can still charge your handheld while using the dual-screen solution!
Interested in modifications for your ROG Ally, but not quite ready to bolt on a second display? Check out this phenomenally documented battery upgrade from an iFixit staffer that we recently covered.