As the old saying goes, there’s no such thing as a lock that can’t be picked. However, it seems like there are plenty of examples of car manufacturers that refuse to add these metaphorical locks to their cars at all — especially when it comes to securing the electronic systems of vehicles. Plenty of modern cars are essentially begging to be attacked as a result of such poor practices as unencrypted CAN busses and easily spoofed wireless keyfobs. But even if your car comes from a manufacturer that takes basic security precautions, you still might want to check out this project from the University of Michigan that is attempting to add another layer of security to cars.
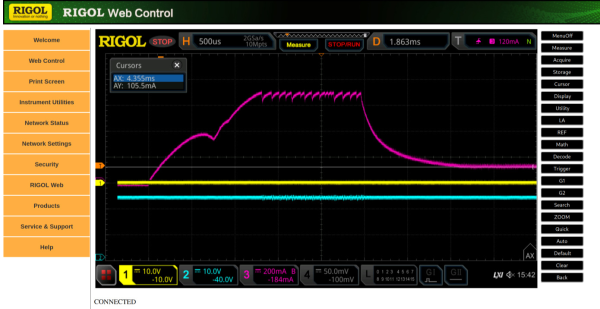
The security system works like many others, by waiting for the user to input a code. The main innovation here is that the code is actually a series of voltage fluctuations that are caused by doing things like turning on the headlights or activating the windshield wipers. This is actually the secondary input method, though; there is also a control pad that can mimic these voltage fluctuations as well without having to perform obvious inputs to the vehicle’s electrical system. But, if the control pad isn’t available then turning on switches and lights to input the code is still available for the driver. The control unit for this device is hidden away, and disables things like the starter motor until it sees these voltage fluctuations.
One of the major selling points for a system like this is the fact that it doesn’t require anything more complicated than access to the vehicle’s 12 volt electrical system to function. While there are some flaws with the design, it’s an innovative approach to car security that, when paired with a common-sense approach to securing modern car technology, could add some valuable peace-of-mind to vehicle ownership in areas prone to car theft. It could even alleviate the problem of cars being stolen via their headlights.
Continue reading “Car Security System Monitors Tiny Voltage Fluctuations”