We’re in the middle of an epic run to award $50,000 in loot to Hackaday Prize entries this summer. This week we doled out a Stickvise low-profile PCB vise to 65 different projects! This actually started out as a really great project on Hackaday.io.
Winners are listed below, please check out their projects; skull the ones you find awesome and leave your words of encouragement as comments on those projects. Then get to work and submit something of your own. Your odds of winning during these weekly giveaways are quite good. Our recommendation for your best chances at winning are to polish up the information you’re sharing — tell the whole story of what you’ve done so far and what you plan to do. Post some images whether pictures of the prototype, renders of what you are working on, or hand-drawn diagrams from the back of a napkin.
Normally we launch the following week’s contest in this winner-announcement post. But we’re changing it up a bit this time around. Look for a post on Monday that shares all the details of what is coming next!
Last Week’s Winners of 65 Stickvise
Each project creator will find info on redeeming their prize as a message on Hackaday.io.
- nRFIoT – Easy IoT Sensors
- AluPi – Pocketable Game and Computer System
- Portable environmental monitor
- Mute-ation
- WΛLLTΞCH PHΛNTOM: Bone-Conduction BT Audio Headset
- Dual Channel Battery Charger/Analyzer
- low-field MRI
- Smart Battery makes a smarter Power Pack
- Indoor air pollution reduction
- A low cost multispectral imaging payload for a UAV
- Medical tricorder
- A tiny scientific calculator
- EZeeSample
- Open Source Industrial Smart Camera
- Eye drive wheelchair
- Teleimperium
- An IOT Device That Tells Dad the Stove is Off.
- DC Motor Controller for CNC Router
- Terra Spider
- Chocometer
- Ultrasonic range finder for the visually impaired
- Sit.Up
- Car alarm secure remote with nRF24LE1
- Bench Power Supply
- Aleph
- Weather Controlled SmartWindow
- ESP8266 Dev-Board
- Health Maintenance Robot
- uBBB 32u4
- BLE Intertial Measurement Unit
- ButlerBOT
- Driverless Mouse and Keyboard Sharing
- Residential Street Speed Watch
- DIY Electric Vehicle from Recycled Parts
- Internet enabled smoke alarm
- ARDUINO MPPT SOLAR CHARGE CONTROLLER
- Python Powered Scientific Instrumentation tool
- USB Booster
- Muffsy Hifi Dual Power Supply
- Pediatric Therapy Device
- DC UPS and Wallwarts Eliminator
- A Wireless I2C Bridge for Amateur Radio Use
- Timstock Slim – a tool for the autistic
- C12666MA Micro-Spectrometer
- Wireless Batteryless Mouse
- Biopotential Signal Library
- Green eutectic rocket propellant
- Portable tiny IoT device solving general problem
- In-Line Battery Back-Up Module for Ham Radio
- Electric Ninja
- Low-noise, Easy-to-use Analog Data Logger: SiGZiG
- Low Cost Wireless Home Automation and Security
- EM-Drive
- NodeUSB- ‘Eat your own dog food’ WiFi IoT DevKit
- PICxie: A micro PIC18F development kit
- BeagleLogic
- Binary Pomodoro Timer
- SentriFarm (Farmer stay in Bed, too hot to reap!)
- ESPLux – Smarts for your downlights
- Guard Llama
- Iconic clock for deaf children
- Braille Computer
- Artificial Muscles and Ultra-capacitors
- MultiSpork
- Tote, affordable spider robot

















 MakerCamp brings 30 talented Makers, Hackers, Designers, and Engineers together for a few days to build a makerspace inside of a shipping container.
MakerCamp brings 30 talented Makers, Hackers, Designers, and Engineers together for a few days to build a makerspace inside of a shipping container. Hackaday Shenzhen Meetup
Hackaday Shenzhen Meetup

 One of the adventures we’ve always wanted to take part in is
One of the adventures we’ve always wanted to take part in is 
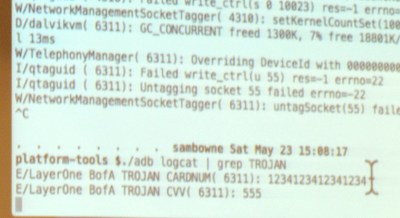
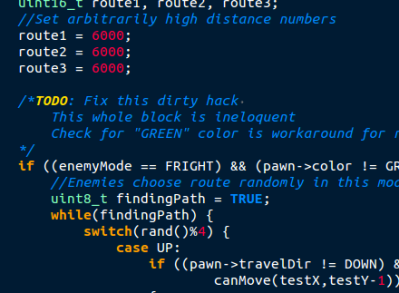
 What is the most troubling is that
What is the most troubling is that 
 A master key for the NYC Subway was compromised and available for sale.
A master key for the NYC Subway was compromised and available for sale.  Worse, was the availability of fire-department
Worse, was the availability of fire-department  [Jos’] example of doing the right thing is to use a “prop” key for news stories. Here he is posing with a key after the talk. Unfortunately this is my own house key, but I’m the one taking pictures and I have blurred the teeth for my own security. However, I was shocked during image editing at the quality of the outline in the image — taken at 6000×4000 with no intent to make something that would serve as a source for a copy. It still came out remarkably clear.
[Jos’] example of doing the right thing is to use a “prop” key for news stories. Here he is posing with a key after the talk. Unfortunately this is my own house key, but I’m the one taking pictures and I have blurred the teeth for my own security. However, I was shocked during image editing at the quality of the outline in the image — taken at 6000×4000 with no intent to make something that would serve as a source for a copy. It still came out remarkably clear.








