An obligatory “Future’s so bright I gotta wear… denim” joke is the only way to kick off this article. Sorry!
Now that that’s out of the way, how would you turn your own blue jeans into sunglasses? Well you wouldn’t, unless you’ve built an intricate jig for assembling sunglasses frames like [Mosevic] has done. Boiled down, this is like making parts out of carbon fiber, except you swap in denim for the carbon fiber. Several layers of blue jean material are layered in a mold and impregnated with resin. Once hardened, parts can be milled or laser cut from this stock and then assembled into the frames all of the hipsters are after.
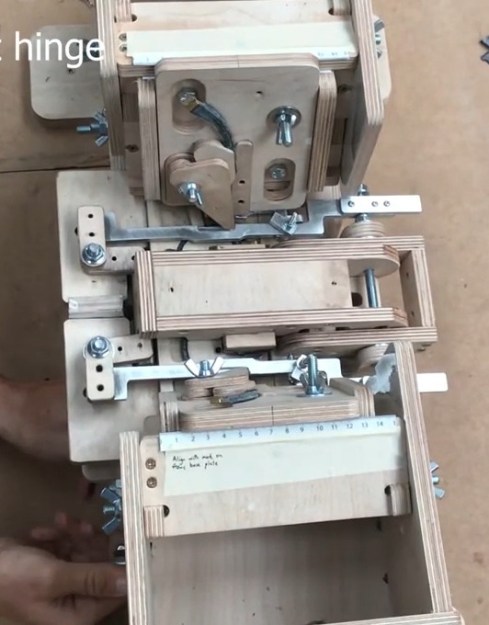 For us its the assembly jig that’s so interesting to see. [Mosevic] shared it in an unlisted video of an update to the Kickstarter campaign which ran at the end of 2019. The jig is used to align machined parts into stack ups that include brass reinforcement and pins to align layers, as well as the joining for the three parts of the frame via the metal hinges. Most of the jig is made from machined plywood. The plates that hold the three parts of the frame, the “frame front” and the two “temples” in eyeglass parlance, are interchangeable so that the same jig can be used to assemble several variants of the frame design. The most notable non-plywood part of the jig are two metal clamps that hold the hinge into the frame front as the glue dries, holding a couple of tiny chunks of denim/resin block in place.
For us its the assembly jig that’s so interesting to see. [Mosevic] shared it in an unlisted video of an update to the Kickstarter campaign which ran at the end of 2019. The jig is used to align machined parts into stack ups that include brass reinforcement and pins to align layers, as well as the joining for the three parts of the frame via the metal hinges. Most of the jig is made from machined plywood. The plates that hold the three parts of the frame, the “frame front” and the two “temples” in eyeglass parlance, are interchangeable so that the same jig can be used to assemble several variants of the frame design. The most notable non-plywood part of the jig are two metal clamps that hold the hinge into the frame front as the glue dries, holding a couple of tiny chunks of denim/resin block in place.
Here you can see the jig with all clamps fully closed. There is not an insignificant amount of time just getting the parts into this jig. But parts still need quite a bit of cleanup after this process to sand, shape, and polish all edges and surfaces of the frames. And of course you have to figure in the time it took to make the parts that went into the jig in the first place. The finished frames are gorgeous, but we have a lot more respect having seen what it takes to pull it off.
Now if you like your glasses like George Washington liked his false teeth, here’s how you can pull a set of shades out of your woodshop.
Continue reading “Denim Sunglasses Frames Use A Wicked Set Of Jigs” →