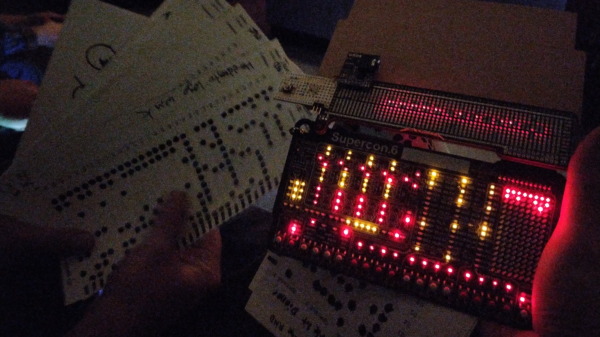
This year’s Hackaday Supercon, the first since 2019 thanks to the pandemic, was a very similar affair to those of the past. Almost every hardware-orientated hacker event has its own custom electronic badge, and Supercon was no different. This year’s badge is a simulation platform for a hypothetical 4-bit CPU created by our own [Voja Antonic], and presented a real challenge for some of the attendees who had never touched machine code during their formative years. The challenge set was to come up with the most interesting hack for the badge, so collaborators [Ben Hencke] and [Zach Fredin] set about nailing the ‘expandr’ category of the competition with their optical punched card reader bolt-on.
Peripheral connectivity is somewhat limited. The idea was to build a bolt-on board with its own local processing — using a PixelBlaze board [Ben] brought along — to handle all the scanning details. Then, once the program on the card was read, dump the whole thing over to the badge CPU via its serial interface. Without access to their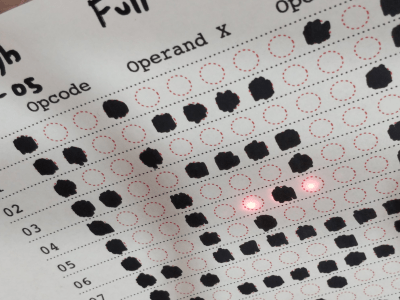 usual facilities back home, [Ben] and [Zach] obviously had to improvise with whatever they had with them, and whatever could be scrounged off other badges or other hardware lying around.
usual facilities back home, [Ben] and [Zach] obviously had to improvise with whatever they had with them, and whatever could be scrounged off other badges or other hardware lying around.
One big issue was that most people don’t usually carry photodiodes with them, but luckily they remembered that an LED can be used as a photodiode when reverse-biased appropriately. Feeding the signal developed over a one Meg resistance, into a transconductance amplifier courtesy of a donated LM358 there was enough variation for the STM32 ADC to reliably detect the difference between unfilled and filled check-boxes on the filled-in program cards.
The CPU required 12-bit opcodes, which obviously implies 12 photodiodes and 12 LEDs to read each word. The PixelBlaze board does not have this many analog inputs. A simple trick was instead of having discrete inputs, all 12 photodiodes were wired in parallel and fed into a single input amplifier. To differentiate the different bits, the illumination LEDs instead were charlieplexed, thus delivering the individual bits as a sequence of values into the ADC, for subsequent de-serialising. The demonstration video shows that it works, with a program loaded from a card and kicked into operation manually. Such fun!
Punch cards usually have a hole through them and can be read mechanically, and are a great way to configure testers like this interesting vacuum valve tester we covered a short while back.