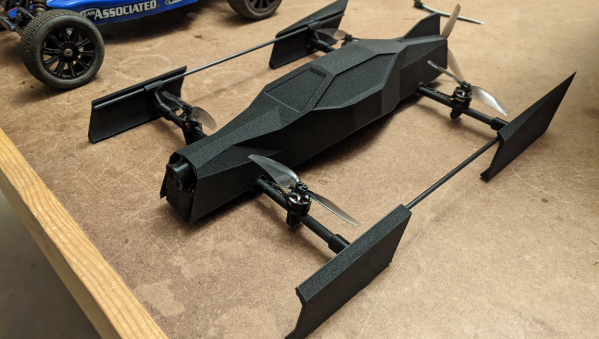
As anyone who’s spent Christmas morning trying to shake a quadcopter out of a tree can attest, controlling these fast moving RC vehicles can be tricky and require a bit of practice to master. [Erik] wanted to simplify this a little bit so his children and friends could race with him, and the end result is a drone that only needs two inputs to fly.
The results of his experimentation with simplifying the controls resulted in a “speeder” type drone which attempts to keep a certain distance off of the ground on its own thanks to an extremely fast time-of-flight sensor. The pilot is then left to control the throttle and the steering only, meaning that [Erik] can use pistol-style RC controllers for these machines. They have some similarities to a quadcopter, but since they need to stay level in flight they also have a fifth propeller on the back, similar to an airboat. This allows for a totally separate thrust control than would normally be available on a quadcopter.
The resulting vehicle is immediately intuitive to fly, behaving more like an RC car than a quadcopter. This also required quite a bit of processing power to compute the proper roll and yaw from a single steering input, but after many prototypes the result is impressive, especially since it was also built to use FPV as a means of control. One of the videos below demonstrates this video, and looks extremely fun to fly, and we wouldn’t mind seeing a race with these types of speeders much like we saw in the past with a group of pod-racing quadrotors.