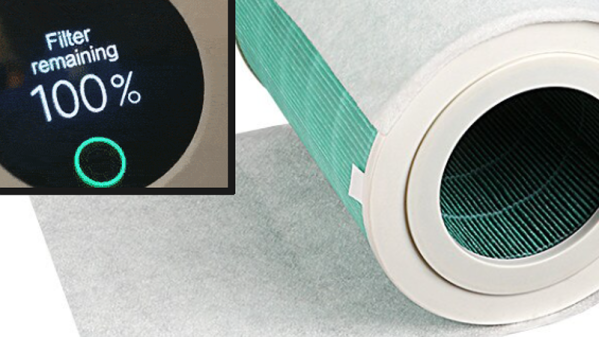
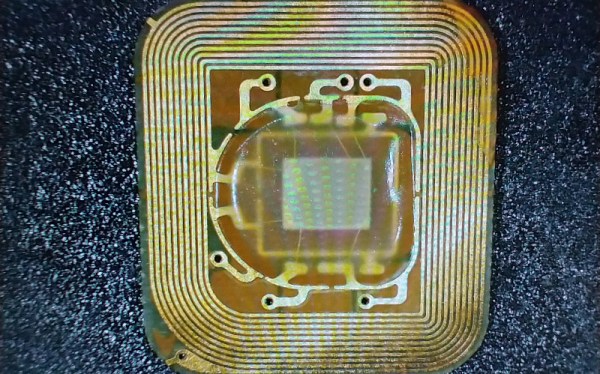
When [Unethical Info] was looking at air purifiers a while back, their eye fell on a Xiaomi 4 Pro, with a purchase quickly made. Fast-forward a while and suddenly the LCD on top of the device was showing a threatening ‘0% filter life remaining’ error message. This was traced back to an NFC (NTAG213) tag stuck to the filter inside the air purifier that had been keeping track of usage and was now apparently the reason why a still rather clean filter was forcibly being rejected. Rather than give into this demand, instead the NFC tag and its contents were explored for a way to convince it otherwise, inkjet cartridge DRM-style.
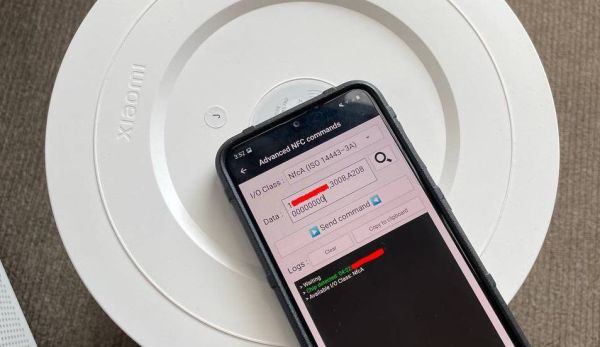
While in the process of reverse-engineering the system and doing some online research, a lucky break was caught in the form of earlier research by [Flamingo Tech] on the Xiaomi Air Purifier 3, who had obtained the password-generating algorithm used with the (password-locked) NFC tag, along with the target area of the filter’s NFC tag to change. Using the UID of the NFC tag, the password to unlock the NFC tag for writing was generated, which requires nothing more than installing e.g. ‘NFC Tools’ on an NFC-capable Android/iOS smartphone to obtain the tag’s UID and reset the usage count on the filter.
A password generating tool is provided with the [Unethical Info] article, and this approach works across a range of Xiaomi air purifiers, making it an easy fix for anyone who owns such a device but isn’t quite ready yet to shell out the big bucks for a fresh DRM-ed filter. This approach also saves one from buying more NFC tags, which was the case with the previous solution.