If you’re an infrastructure dweeb, it’s hard to drive past an electrical substation and not appreciate the engineering involved in building something like that. A moment’s thought will also make it hard to miss just how vulnerable a substation is to attack, especially those located way out in the hinterlands. And now we’re learning that late year, someone in Pennsylvania noticed this vulnerability and acted on it by attacking a substation with a commercial drone. Rather than trying to fly explosives over the substation fence, the attacker instead chose to dangle a copper wire tether under the drone, in an attempt to cause a short circuit. The attempt apparently failed when the drone crashed before contacting any conductors, and the attacker appears to have been ignorant of the extensive protective gear employed at substations that likely would have made a successful attack only a temporary outage. But it still points to the vulnerability of the grid to even low-skill, low-cost attacks.
We’ve probably all had the experience of using someone’s janky app and thinking, “Pfft! I could write something better than this!” That’s what a bunch of parents of school-age kids in Sweden thought, and they went ahead and did exactly that. Unfortunately, it didn’t turn out quite the way they expected. The problem app was called Skolplattform, which was supposed to make it easy for Stockholm’s parents to keep track of their kids’ progress at school. The app, which cost 1 billion Swedish Krona to develop, is by all accounts a disaster. But some frustrated parents managed to reverse engineer the API and build a new, better one on top of it. This resulted in Öppna Skolplattformen, an open-source app that actually works. Not to be upstaged, the city of Stockholm accused the parents of cyber crimes and data breaches. They also engaged the parents in an “API war”, constantly changing their system to nerf the new app and forcing the parents to rewrite it. In the end, the parents won, with Stockholm changing its position after a police report found that all data being accessed were voluntarily made public by the city. But it’s still a cautionary tale about the dangers of one-upping The Man.
Sam Battles is in a bit of a moral bind, and it’s something that others in our community may run into. Sam is perhaps better known as “Look Mum, No Computer” on YouTube, and as the proprietor of the “This Museum Is (Not) Obsolete” showcase of retro technology in England. He’s also an avid builder of analog synthesizers, including a world-record synth with a thousand oscillators called the “Megadrone.” He’d like to tackle another build to try to break his own records, but in a time of fragile supply chains and other woes too numerous to mention, doing so would likely require the world’s entire supply of some components. Hence the dilemma: do any of us as hobbyists have a moral obligation to tread lightly when it comes to component selection? It’s an interesting question, and one that’s sure to engender strong opinions, which of course we encourage you to share in the comments section. Please just try to keep it civil.


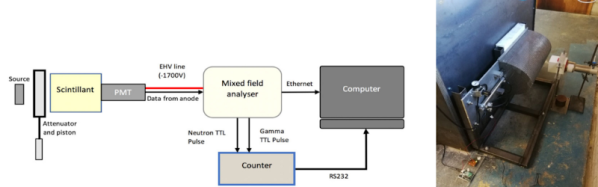


 How was this accomplished? First of all, Winston and his team researched the correct “look” for the splash impacts by firing projectiles into mud and painstakingly working to duplicate the resulting shapes. These realistic-looking crater sculpts were then cast in some mixture of foam rubber, and given a chromed look by way of vacuum metallizing (also known as
How was this accomplished? First of all, Winston and his team researched the correct “look” for the splash impacts by firing projectiles into mud and painstakingly working to duplicate the resulting shapes. These realistic-looking crater sculpts were then cast in some mixture of foam rubber, and given a chromed look by way of vacuum metallizing (also known as