We’ve all been there. A big bag of resistors all mixed up. Maybe you bought them cheap. Maybe your neatly organized drawers spilled. Of course, you can excruciatingly read the color codes one by one. Or use a meter. But either way, it is a tedious job. [Ishann’s] solution was to build an automatic sorter that directly measures the value using a voltage divider, rather than rely on machine vision as is often the case in these projects. That means it could be modified to do matching for precise circuits (e.g., sort out resistors all marked 1K that are more than a half-percent away from one nominal value).
There is a funnel that admits one resistor at a time into a test area where it is measured. A plate at the bottom rotates depending on the measured value. In the current implementation, the resistor either falls to the left or the right. It wouldn’t be hard to make a rotating tray with compartments for different values of resistance. It looks like you have to feed the machine one resistor at a time, and automating that sounds like a trick considering how jumbled loose axial components can be. Still, its a fun project that you probably have all the parts to make.
An Arduino powers the thing. An LCD screen and display control the action. If you want some practice handling material robotically, this is a great use of servos and gravity and it does serve a practical purpose.
We have seen many variations on this, including ones that read the color code. If you ever wanted to know where the color code for resistors came from, we took a trip to the past to find out earlier this year.










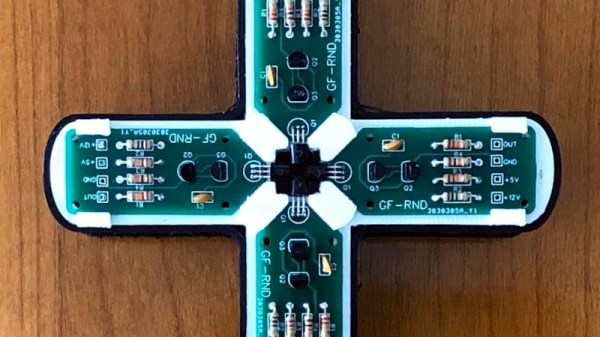
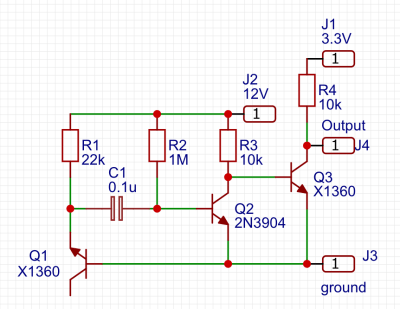 One of the simplest circuits for generating random analogue noise involves a reverse biased diode in either Zener or avalanche breakdown, and it is a variation on this that he’s using. A reverse biased emitter junction of a transistor produces noise which is amplified by another transistor and then converted to a digital on-off stream of ones and zeroes by a third. Instead of a shift register to create his four bits he’s using four identical circuits, with no clock their outputs randomly change state at will.
One of the simplest circuits for generating random analogue noise involves a reverse biased diode in either Zener or avalanche breakdown, and it is a variation on this that he’s using. A reverse biased emitter junction of a transistor produces noise which is amplified by another transistor and then converted to a digital on-off stream of ones and zeroes by a third. Instead of a shift register to create his four bits he’s using four identical circuits, with no clock their outputs randomly change state at will.