You’ve got to walk before you can run, right? Perhaps not, if this bipedal dino-like running robot is any indication.
Officially dubbed a “Planar Elliptical Runner,” the bot is a test platform for bipedal locomotion from the Institute for Human and Machine Cognition. Taking inspiration from the gait of an ostrich — we think it looks more like a T. rex or velociraptor, but same difference — [Jerry Pratt]’s team at IHMC have built something pretty remarkable. Contrary to all the bipedal and quadrupedal robots we’ve seen, like Boston Dynamics’ Big Dog and PETMAN, which all fairly bristle with sensors and actuators, the PER is very stripped down.
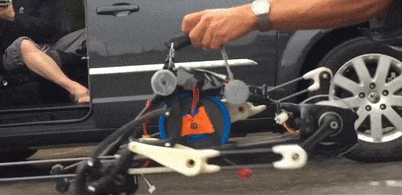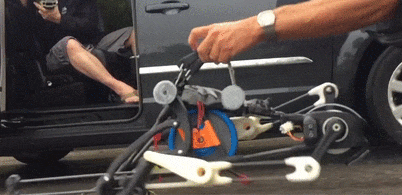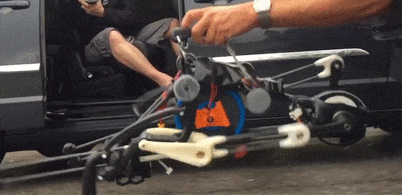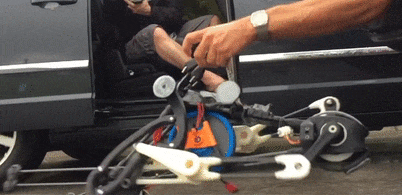 A single motor runs the entire drive chain using linkages that will look familiar to anyone who has taken an elliptical trainer apart, and there’s not a computer or sensor on board. The PER keeps its balance by what the team calls “reactive resilience”: torsion springs between the drive sprocket and cranks automatically modulate the power to both the landing leg and the swing leg to confer stability during a run. The video below shows this well if you single-frame it starting at 2:03; note the variable angles of the crank arms as the robot works through its stride.
A single motor runs the entire drive chain using linkages that will look familiar to anyone who has taken an elliptical trainer apart, and there’s not a computer or sensor on board. The PER keeps its balance by what the team calls “reactive resilience”: torsion springs between the drive sprocket and cranks automatically modulate the power to both the landing leg and the swing leg to confer stability during a run. The video below shows this well if you single-frame it starting at 2:03; note the variable angles of the crank arms as the robot works through its stride.
The treadmill tests are constrained by a couple of plastic sheets, but the next version will run free. It’s not clear yet how directional control will be achieved, not is it obvious how the PER will be able to stop running and keep its balance. But it’s an interesting advance in locomotion and we look forward to seeing what IHMC’s next trick will be.
Continue reading ““Look Ma, No Gyros!”: A Self-Balancing Mechanical Velociraptor”


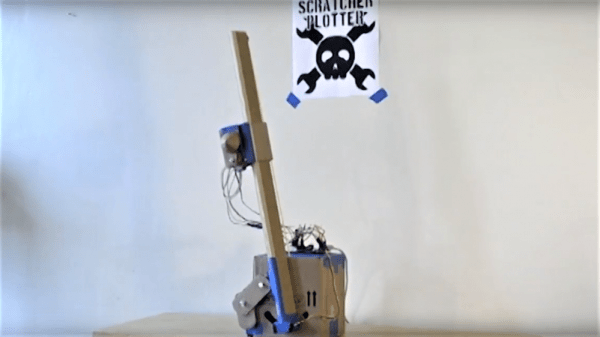
 [VijeMiller] has aluminum extrusion tastes on a cardboard budget, but don’t let that put you off this clever build. The idea is pretty simple: a two-axis plotter that moves a rotary-action business end to any point within a V-shaped work envelope. The Arduino in the base talks to a smartphone app that lets you point to exactly the spot in need of attention on what for most of us would be an incredibly optimistic photorealistic map of the dorsal aspect of the body (mildly NSFW photo in the link above dips below the posterior border). Point, click, sweet relief.
[VijeMiller] has aluminum extrusion tastes on a cardboard budget, but don’t let that put you off this clever build. The idea is pretty simple: a two-axis plotter that moves a rotary-action business end to any point within a V-shaped work envelope. The Arduino in the base talks to a smartphone app that lets you point to exactly the spot in need of attention on what for most of us would be an incredibly optimistic photorealistic map of the dorsal aspect of the body (mildly NSFW photo in the link above dips below the posterior border). Point, click, sweet relief.

 [Nick] is designing a new kind of RepRap,
[Nick] is designing a new kind of RepRap, 











