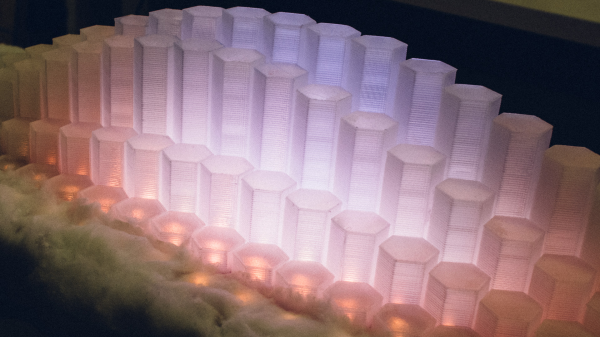
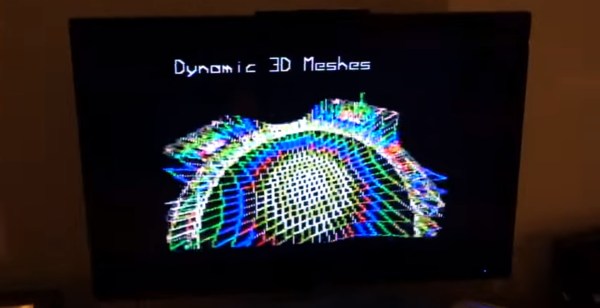
[Norwegian Creations] makes things as a business model. Tired of the mundane lamp above their heads, they decided to put their skills to use. The basic idea was simple, plot out a cool 3D function, put some RGB LEDs behind it, make it an awesome mathematical rainbow light display, hang it right above their desks, and then ignore it for their monitors while they worked.
The brains of the project is a Raspberry Pi B+, WS2812 LED strips, and a Fadecandy controller from Adafruit. They 3D printed hexagonal towers out of clear plastic and labeled each carefully. Then they attached the strips to the board, glued on the hexagons, and covered the remaining surface in cotton balls to give it a cloud-like appearance.
The lamp normally plays patterns or maintains a steady light. As the day turns to night it reflects the world outside. However, if someone likes their Facebook page the light has a little one robot strobe party, which we imagine can get annoying over time. Video after the break.
Continue reading “Building An Interactive LED Lamp To Annoy Yourself”