A few semesters back, [Jordan] was in an Intro to Hardware Security course at CMU. The final project was open ended, and where some students chose projects like implementing a crypto algorithm or designing something on an FPGA, [Jordan] decided to do something a little more ambitious. He wanted to decapsulate and reverse engineer an IC. No, this isn’t taking a peek at billions of transistors — [Jordan] chose a 74-series Quad XOR for this project — but it does show what goes into reverse engineering silicon, and how even simple chips can be maddeningly confusing.
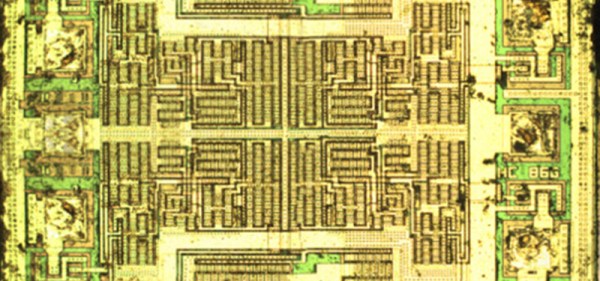
The first step to reverse engineering a chip is decapsulation, and for this [Jordan] had two options. He could drop acid, or he could attack a ceramic package with an endmill. While hot nitric acid is effective and fun, it is a bit scary, so [Jordan] mounted a few chips in a 3D printed holder wedged in the vice on his mill. By slowly bringing the Z axis down a few thou at a time, he was able to find the tiny 1 mm square bit of silicon embedded in this chip. With the help of a grad student and the cleanroom, this square of sand was imaged with a very nice microscope.
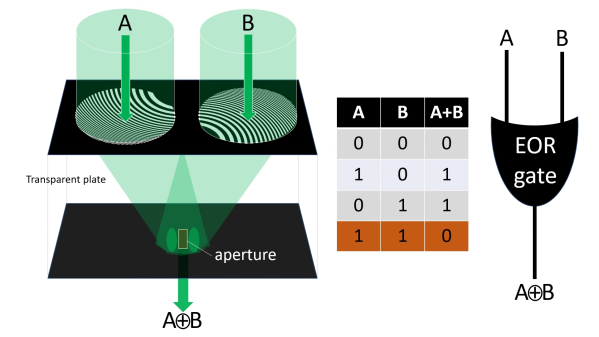
Now that [Jordan] had an image of the silicon itself, he had to reverse engineer the chip. You might think that with less than a dozen transistors in there, designing an XOR out of transistors is something anyone with a bit of Minecraft experience can do. This line of thinking proved to be a trap. Technically, this wasn’t an XOR gate. It was a transmission gate XNOR gate with a big inverter on the output. Logically, it’s the same, but when it comes to silicon fabrication, the transmission gate XNORs aren’t able to sink or source a lot of current. By designing the chip as an XNOR with an inverter, the chip designers were able to design a simple chip that could still meet the spec.
While [Jordan] managed to reverse engineer the chip, this was quite possibly the simplest chip he could reverse engineer. The Quad XOR is just the same silicon repeated four times, anyway. This is the baseline for all efforts to reverse engineer silicon, and there were still a few confusing traps.