[Henrik Langer] put his powerful audio acquisition and output board up on Hackaday.io, and we thought we’d point it out to you. It’s one of those projects that used to be pro audio just a few years back, but is doable (and affordable) DIY today: dual stereo inputs and four(!) stereo outputs, all sampled at 24 bits and up to 192 kHz. It’s configured as a BeagleBone cape, and comes with a customized Linux distribution for the ‘Bone.
What would you do with such a thing? It’s essentially a recording studio in your pocket, with a computer attached. The video (linked below the break) demonstrates using the device as a real-time stereo delay effect unit, but that’s only making use of one channel. Between effects, recording, and then all sorts of much-better-than-CD quality sound synthesis and playback possibilities, it’s an open-ended audio playground.
And all that from what is essentially a (very well-done) breakout board for a fancy DAC/ADC chip from Analog Devices: the AD1938. We’d love to have one of these on our desktop. Check out [Henrik]’s GitHub for the PCB and build instructions and BOM and everything else you’d need to get started. Very nice job!



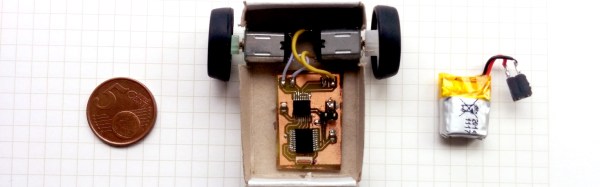


 The current iteration is complete and builds upon
The current iteration is complete and builds upon