When you don’t want to use I2C or SPI, and MIDI and DMX are old hat, [Scott] comes along and invents a very strange networking protocol that is just daisy chaining a few Arduinos together with serial connections.
Strange as it may seem, this networking protocol actually makes a whole lot of sense. [Scott] is working on an animatronic birdhouse in the vein of Disney’s Imagineers and needed to network a whole bunch of Arduinos without using up precious IO pins.
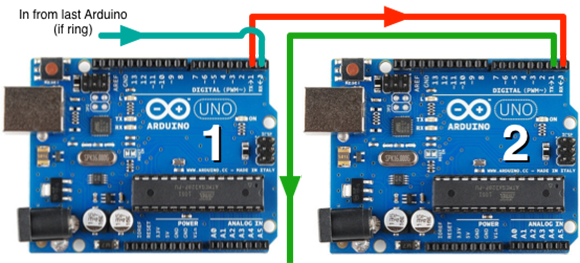
The networking stack [Scott] came up with capitalizes on the hardware UART in each Arduino by simply daisy-chaining several boards together. By adding an FTDI breakout at the beginning of the chain, [Scott] can control dozens of Arduinos straight from a terminal
[Scott] isn’t using off-the-shelf Arduinos for this project – a few months ago he found 100 Arduino-compatible stepper motor controllers while dumpster diving at his job, giving him more than enough nodes to come up with some pretty crazy networking protocols. It’s a great use of the hardware he has on hand, and a very clever solution to controlling dozens of microcontrollers at once.
Check out [Scott]’s demo after the break.
Continue reading “Inventing Networking Protocols For Dozens Of Arduinos”