If you’ve ever had to repair an iPhone for a friend, you’ll know they have a ridiculous number of screws. Most companies standardize screws in their products, but since Apple doesn’t expect you to fix a phone yourself… they may have let this one slide.
You see, each of these screws is different.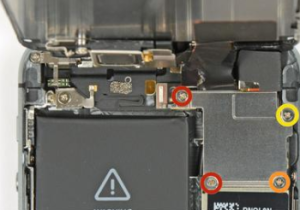 The red ones are 1.7mm long, the yellow one, 1.3mm, and the orange one, 1.2mm.
The red ones are 1.7mm long, the yellow one, 1.3mm, and the orange one, 1.2mm.
Guess what happens if you install either red or yellow screws into the orange spot, since your eyesight isn’t good enough to notice a 0.1mm difference? The screw will cut into the PCB and break several 50 micron traces, as shown in the picture above, causing a blue screen error on the phone.
Fun stuff.
[Sam Schmidt] is the owner of a repair outfit called iRepairNational, and he and his team spent a day trying to figure out the problem – it’s not exactly easy to spot. They’ve managed to repair it by cutting thin strips of copper foil (the width of a human hair) and floating it into place using the surface tension of the flux they were using for soldering. On average it takes them around 2 hours to do the repair, though they’ve done a few in just under an hour.
Since discovering and sharing the problem, they’ve had customers around the world sending in phones for repair – often at the fault of someone else trying to repair something completely different in the phone, and then using the wrong screw as they put it all back together.



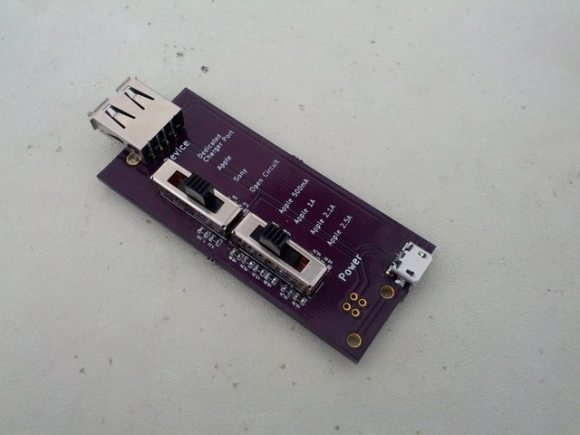 Oooh, look, a public charging station. Should you trust it? You might get juice jacked. Oh wait, you’ve got a
Oooh, look, a public charging station. Should you trust it? You might get juice jacked. Oh wait, you’ve got a