Air Traffic Controllers use Automatic Dependent Surveillance-Broadcast (ADS-B) as an alternative to secondary radar to track aircraft. The ADS-B is transmitted by the aircraft and contains information such as GPS position, pressure, altitude, and callsign among other things at a 1090 MHz frequency, which can be decoded using any of a number of software tools.
[Mike Field] lives near an airport, and decided he wanted to peek into the tracking signals for fun. He turned to an RTL-based TV Dongle. Since the stock antenna was not cutting it, he decided to make one specifically for the 1090 MHz signal. His design is based on Coaxial Collinear Antenna for ADS-B Receiver by [Dusan Balara] which uses pieces of the coaxial cable cut to the right length. There are a number of calculations involved in determining the size of the cable, however, the hack in this design is the way he uses a USB based oscilloscope to measure the speed of RF waves inside the line in question.
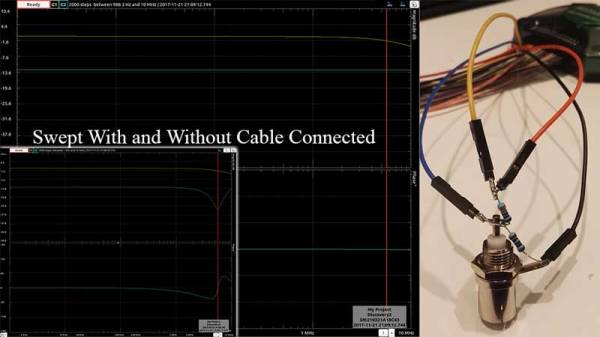
We reached out to [Mike], and this is what he had to say. The idea is to use a cable of half the size of the wavelength which is calculated as
lambda = c/f
For the best reception, the sections of coax need to be half a wavelength long – but the wavelength of the signal inside the coax, which is shorter than the wavelength in free space. As this was a generic cable he had no idea of the dielectric that separates the core from the shield, so the ‘velocity factor’ could be anything depending on the exact composition.
To determine the speed of the signal in the cable, his approach omits the more expensive equipment. A length of coax acts as a stub – any energy that is sent into the cable reaches the far end of the transmission line and is then reflected back to the source. When the cable is 1/4th of the wavelength long, the reflected signal arrives back at the start of the signal 180 degrees out of phase – in a perfect world it would completely null out the input signal. Continue reading “Measuring HF Signal Speeds In A DIY Coaxial Collinear Antenna” →