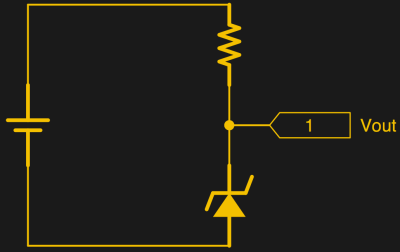
For the longest time, Zener diode regulators have been one of those circuits that have been widely shared and highly misunderstood. First timers have tried to use it to power up their experiments and wondered why things did not go as planned. [James Lewis] has put up a worth tutorial on the subject titled, “Zener Diode makes for a Lousy Regulator” that clarifies the misconceptions behind using the device.
[James Lewis] does an experiment with a regulator circuit with an ESP8266 after a short introduction to Zener diodes themselves. For the uninitiated, the Zener diode can operate in the reverse bias safely and can do so at a particular voltage. This allows for the voltage across the device to be a fixed value.
This, however, depends on the current flowing through the circuit which in turn relies on the load. The circuit will work as expected for loads the draw a small amount of current. This makes it suitable for generating reference voltages for microcontrollers and such.
To make a Zener into a “proper” voltage regulator, you just need to buffer the output with an amplifier of some kind. A single transistor is the bare minimum, but actually can work pretty well. You might also add a capacitor in parallel with the Zener to smooth out some of its noise.
Zener diodes are wonderful little devices and write-ups like these are indispensable for beginners and should be shared more often like the Zener and Schottky Tutorial and Diodes as a Switch.