The Apple AirTag is a $29 Bluetooth beacon that sticks onto your stuff and helps you locate it when lost. It’s more than just a beeper though, the idea is that it can be silently spotted by any iDevice — almost like a crowd-sourced mesh network — and its owner alerted of its position wherever they are in the world.
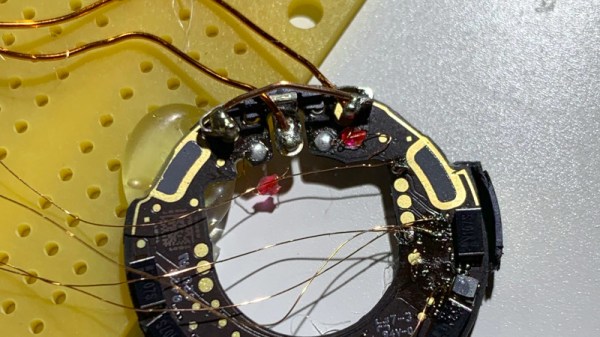
There are so many questions about its privacy implications despite Apple’s reassurances, so naturally it has been of great interest to those who research such things. First among those working on it to gain control of its nRF52832 microcontroller is [Stacksmashing], who used a glitching technique whereby the chip’s internal power supply is interrupted with precise timing, to bypass the internally enabled protection of its debug port. The firmware has been dumped, and of course a tag has been repurposed for the far more worthwhile application of Rickrolling Bluetooth snoopers.
The idea of a global network of every iDevice helping reunite owners with their lost possessions is on the face of it a very interesting one, and Apple are at great pains on the AirTag product page to reassure customers about the system’s security. On one hand this work opens up the AirTag as a slightly expensive way to get an nRF microcontroller for other applications, but the real value will come as the firmware is analysed to see how at the tag itself works.
[Stacksmashing] has appeared on these pages many times before, often in the context of Nintendo hardware. Just one piece of work is the guide to opening up a Nintendo Game and Watch.

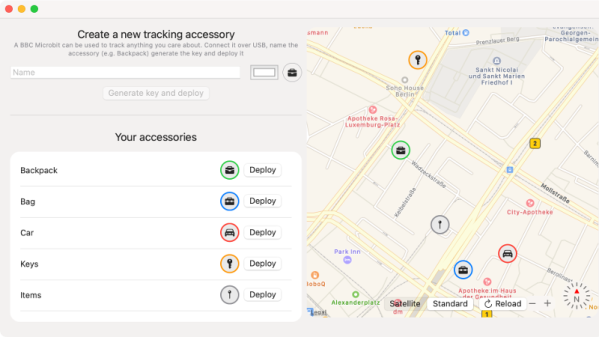
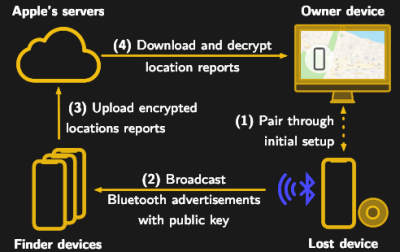 Somewhat ironically, while OpenHaystack allows you to track non-Apple devices on the Find Me tracking network, you will need a Mac computer to actually see where your device is. The team’s software requires a computer running macOS 11 (Big Sur) to run, and judging by the fact it integrates with Apple Mail to pull the tracking data through a private API, we’re going to assume this isn’t something that can easily be recreated in a platform-agnostic way.
Somewhat ironically, while OpenHaystack allows you to track non-Apple devices on the Find Me tracking network, you will need a Mac computer to actually see where your device is. The team’s software requires a computer running macOS 11 (Big Sur) to run, and judging by the fact it integrates with Apple Mail to pull the tracking data through a private API, we’re going to assume this isn’t something that can easily be recreated in a platform-agnostic way.