Even those readers who are most skeptical of Apple products will like this Bluetooth Low Energy (BLE)-enabled iOS app tutorial from [Akio].
With everything being “connected” these days smartphone applications are of course a ubiquitous part of our existence. We’ve seen plenty of examples connecting your Bluetooth-enabled projects to an Android device, but comparatively fewer tutorials for connecting to iOS devices. This mostly has to do with Android’s much larger market share and also Android’s more open-source friendly business model. Nevertheless, if you do much IoT development either as a hobby or professionally, then you probably find yourself interacting with Apple devices more than you like to admit.
[Akio’s] app is essentially updating a chart, in real-time, with data read from an Adafruit nRF52832 Feather board. He then walks you through all the basics of creating a user interface (UI) using Apple’s Storyboard interface, a simple drag-and-drop scheme similar to something you’ve probably used in many other contexts. [Akio] shows readers how to add buttons for allowing users to interact with the app, labels for displaying data to the user, as well as walks you through Apple’s odd methodology of connecting UI elements to code using IBAction and IBOutlets. The highlight of his tutorial is showing readers how to add charts to their iOS apps which seems to take a few more steps than you might imagine.
[Akio] does a really good job detailing all the relevant functions so that readers will hopefully understand what each piece of the code is doing. And we really enjoyed him adding individual video tutorials for some of the trickier programming steps. He also readily admits that some folks may opt to develop their UI exclusively in code as opposed to the Storyboard but he argues that the Storyboard is still important for beginners and is really handy when the UI is fairly simple.
Of course, in true open-source fashion, [Akio] provides all his code on his GitHub repository so you can clone the repo and run the code yourself as well as credit some of the resources he used while making his app. Two things we really love to see. Hopefully, [Akio’s] tutorial will make connecting to iOS devices seem much less onerous than it once was.



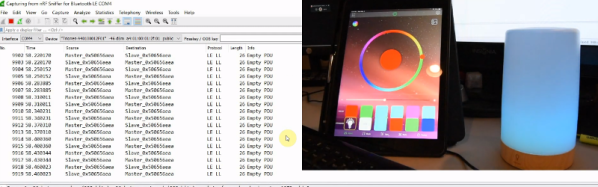
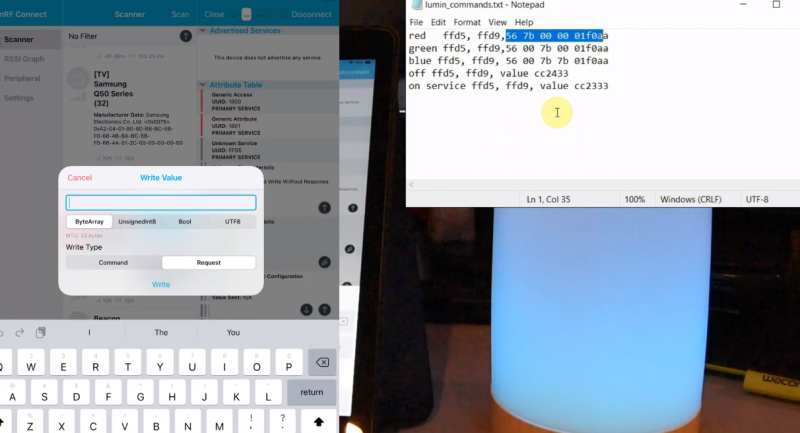
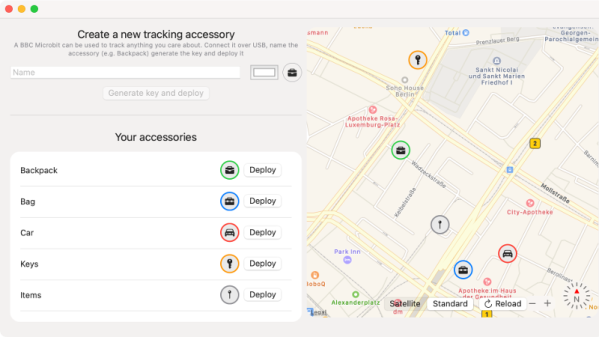
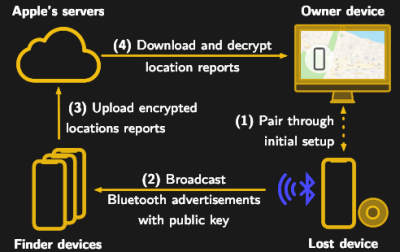 Somewhat ironically, while OpenHaystack allows you to track non-Apple devices on the Find Me tracking network, you will need a Mac computer to actually see where your device is. The team’s software requires a computer running macOS 11 (Big Sur) to run, and judging by the fact it integrates with Apple Mail to pull the tracking data through a private API, we’re going to assume this isn’t something that can easily be recreated in a platform-agnostic way.
Somewhat ironically, while OpenHaystack allows you to track non-Apple devices on the Find Me tracking network, you will need a Mac computer to actually see where your device is. The team’s software requires a computer running macOS 11 (Big Sur) to run, and judging by the fact it integrates with Apple Mail to pull the tracking data through a private API, we’re going to assume this isn’t something that can easily be recreated in a platform-agnostic way.