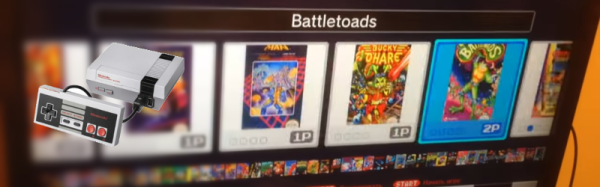
The hype around the NES Classic in 2016 was huge, and as expected, units are already selling for excessively high prices on eBay. The console shipped with 30 games pre-installed, primarily first-party releases from Nintendo. But worry not — there’s now a way to add more games to your NES Classic!
Like many a good hack, this one spawned from a forum community. [madmonkey] posted on GBX.ru about their attempts to load extra games into the console. The first step is using the FEL subroutine of the Allwinner SOC’s boot ROM to dump the unit’s flash memory. From there, it’s a matter of using custom tools to inject extra game ROMs before reburning the modified image to the console. The original tool used, named hakchi, requires a Super Mario savegame placed into a particular slot to work properly, though new versions have already surfaced eliminating this requirement.
While this is only a software modification, it does come with several risks. In addition to bricking your console, virus scanners are reporting the tools as potentially dangerous. There is confusion in the community as to whether these are false positives or not. As with anything you find lurking on a forum, your mileage may vary. But if you just have to beat Battletoads for the umpteenth time, load up a VM for the install process and have at it. This Reddit thread (an expansion from the original pastebin instructions) acts as a good starting point for the brave.
Only months after release, the NES Classic is already a fertile breeding ground for hacks — last year we reported on this controller mod and how to install Linux. Video of this ROM injection hack after the break.