Internet of Things startup Garadget remotely bricked an unhappy customer’s WiFi garage door for giving a bad Amazon review and being rude to company reps. Garadget device owner [Robert Martin] found out the hard way how quickly the device can turn a door into a wall. After leaving a negative Amazon review, and starting a thread on Garadget’s support forum complaining the device didn’t work with his iPhone, Martin was banned from the forum until December 27, 2019 for his choice of words and was told his comments and bad Amazon review had convinced Garadget staff to ban his device from their servers.
The response was not what you would expect a community-funded startup. “Technically there is no bricking, though,” the rep replied. “No changes are made to the hardware or the firmware of the device, just denied use of company servers.” Tell that to [Robert] who can’t get into his garage.
This caused some discontent amoung other customers wondering if it was just a matter of time before more paying customers are subjected to this outlandish treatment. The Register asked Garadget’s founder [Denis Grisak] about the situation, his response is quoted below.
It was a Bad PR Move, Martin has now had his server connection restored, and the IOT upstart has posted a public statement on the matter.– Garadget
This whole debacle brings us to the conclusion that the IoT boom has a lot of issues ahead that need to be straightened out especially when it comes to ethics and security. It’s bad enough to have to deal with the vagaries of IoT Security and companies who shut down their products because they’re just not making enough money. Now we have to worry about using “cloud” services because the people who own the little fluffy computers could just be jerks.





 Fail of the Week is a Hackaday column which celebrates failure as a learning tool. Help keep the fun rolling by writing about your own failures and
Fail of the Week is a Hackaday column which celebrates failure as a learning tool. Help keep the fun rolling by writing about your own failures and 
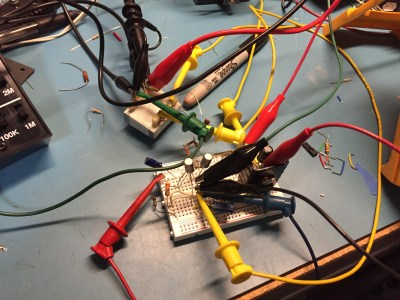 Lets use some cool retro transistors! I merrily go along for hours designing away. Carefully balancing the current of the long tailed pair input. Picking just the right collector power resistor and capacitor value to drive the transformer. Calculating the negative feedback circuit for proper low frequency cutoff and high frequency stability, and into the breadboard the parts go — jumper clips, meter probes, and test leads abound — a truly joyful event.
Lets use some cool retro transistors! I merrily go along for hours designing away. Carefully balancing the current of the long tailed pair input. Picking just the right collector power resistor and capacitor value to drive the transformer. Calculating the negative feedback circuit for proper low frequency cutoff and high frequency stability, and into the breadboard the parts go — jumper clips, meter probes, and test leads abound — a truly joyful event.









