We’ve all seen those chess computers that consist out of a physical playing field, and a built-in computer that would indicate where you should put its pieces while inputting the position of your pieces in some way. These systems are usually found in a dusty cardboard box in a back room’s closet, as playing like this is fairly cumbersome, and a lot depends on the built-in chess computer.
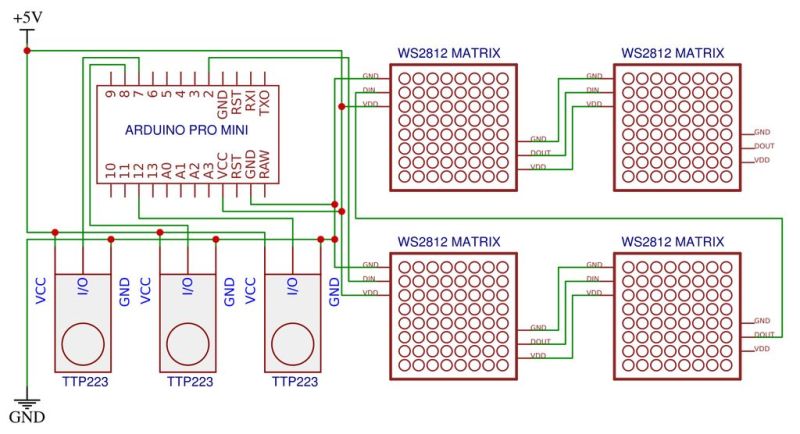
This take by [andrei.erdei] on this decades-old concept involves an ATmega328p-based Arduino Pro Mini board, a nice wooden frame, and 4 WS2812-based 65×65 mm RGB 8×8 LED matrices, as well as some TTP223 touch sensors that allow one to control the on-board cursor. This is the sole form of input: using the UP and RIGHT buttons to select the piece to move, confirm with OK, then move to the new position. The chess program will then calculate its next position and indicate it on the LED matrix.
Using physical chess pieces isn’t required either: each 4×4 grid uses a special pattern that indicates the piece that occupies it. This makes it highly portable, but perhaps not as fun as using physical pieces. It also kills the sheer joy of building up that collection of enemy pieces when you’ve hit that winning streak. You can look at the embedded gameplay video after the break and judge for yourself.
Continue reading “A Colorful Way To Play Chess On An ATmega328”