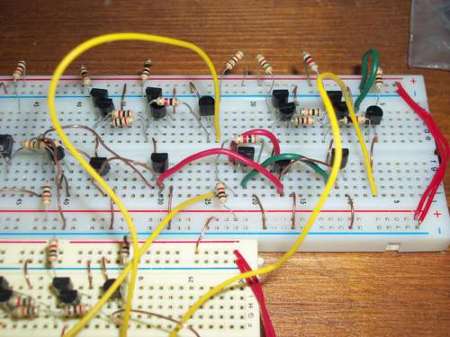
If you’ve ever wanted to dive in and take a look at how memory hardware is implemented here is a good example of how to implement some latching circuits with ether BJT or CMOS transistors. BJTs require biasing resistors which increases the complexity and power consumption when compared to CMOS. If power consumption isn’t an issue you could certainly make some really fast logic.
Most modern on chip RAM is made using SRAM because it only takes six transistors to implement(vs eight) and is pretty fast. When it comes to density DRAM can get one bit of storage by using a single transistor and capacitor(putting the capacitor underneath he transistor can save even more space). All that said, latches and flip flops are still a very useful (and common) tool when working with digital circuits.