An Australian teen is in hot water after he allegedly exposed sensitive medical information concerning COVID-19 patients being treated in a local hospital. While the authorities in Western Australia were quick to paint the unidentified teen as a malicious, balaclava-wearing hacker spending his idle days cracking into secure systems, a narrative local media were all too willing to parrot, reading down past the breathless headlines reveals the truth: the teen set up an SDR to receive unencrypted POCSAG pager data from a hospital, and built a web page to display it all in real-time. We’ve covered the use of unsecured pager networks in the medical profession before; this is a well-known problem that should not exactly take any infosec pros by surprise. Apparently authorities just hoped that nobody would spend $20 on an SDR and an afternoon putting it all together rather than address the real problem, and when found out they shifted the blame onto the kid.
Speaking of RF hacking, even though the 2020 HOPE Conference is going virtual, they’ll still be holding the RF Hacking Village. It’s not clear from the schedule how exactly that will happen; perhaps like this year’s GNU Radio Conference CTF Challenge, they’ll be distributing audio files for participants to decode. If someone attends HOPE, which starts this weekend, we’d love to hear a report on how the RF Village — and the Lockpicking Village and all the other attractions — are organized. Here’s hoping it’s as cool as DEFCON Safe Mode’s cassette tape mystery.
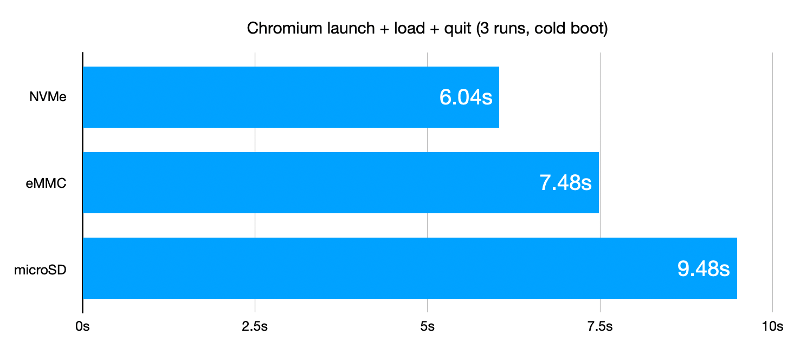
It looks like the Raspberry Pi family is about to get a big performance boost, with Eben Upton’s announcement that the upcoming Pi Compute Module 4 will hopefully support NVMe storage. The non-volatile memory express spec will allow speedy access to storage and make the many hacks Pi users use to increase access speed unnecessary. While the Compute Modules are targeted at embedded system designers, Upton also hinted that NVMe support might make it into the mainstream Pi line with a future Pi 4A.
Campfires on the sun? It sounds strange, but that’s what solar scientists are calling the bright spots revealed on our star’s surface by the newly commissioned ESA/NASA Solar Orbiter satellite. The orbiter recently returned its first images of the sun, which are extreme closeups of the roiling surface. They didn’t expect the first images, which are normally used to calibrate instruments and make sure everything is working, to reveal something new, but the (relatively) tiny bright spots are thought to be smaller versions of the larger solar flares we observe from Earth. There are some fascinating images coming back from the orbiter, and they’re well worth checking out.
And finally, although it’s an old article and has nothing to do with hacking, we stumbled upon Tim Urban’s look at the mathematics of human relations and found it fascinating enough to share. The gist is that everyone on the planet is related, and most of us are a lot more inbred than we would like to think, thanks to the exponential growth of everyone’s tree of ancestors. For example, you have 128 great-great-great-great-great-grandparents, who were probably alive in the early 1800s. That pool doubles in size with every generation you go back, until we eventually — sometime in the 1600s — have a pool of ancestors that exceeds the population of the planet at the time. This means that somewhere along the way, someone in your family tree was hanging out with someone else from a very nearby branch of the same tree. That union, likely between first or second cousins, produced the line that led to you. This is called pedigree collapse and it results in the pool of ancestors being greatly trimmed thanks to sharing grandparents. So the next time someone tells you they’re descended from 16th-century royalty, you can just tell them, “Oh yeah? Me too!” Probably.