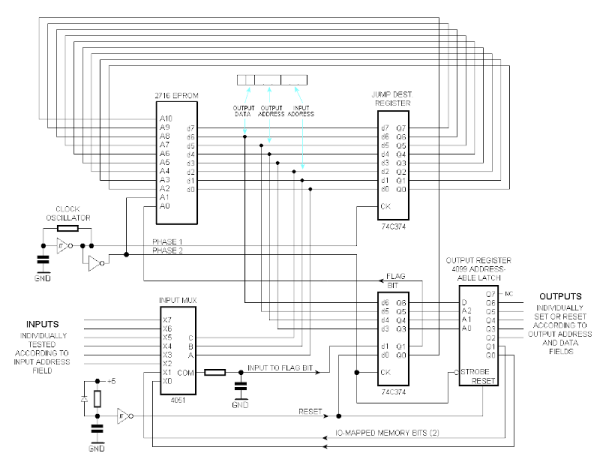
That EPROMs, EEPROMs and kin can be used as programmable logic should probably not come as a major surprise, but [Jimmy] has created a Lisp-based project that makes using these chips as a logic array very straightforward. All it takes is importing the package into one’s Lisp project and defining the logic, before the truth function generates the binary file that can be written to the target chip.
Suggested is the one-time-programmable AT27C512R EPROM (64k x8), but any 8-bit parallel interface (E)EPROM should work, with non-OTP chips being nice unless the chip has to go into a production device. A possible future improvement is the addition of 16-bit (E)EPROM support.
The use of EEPROMs is common with PLA-replacements, as with, for example, the Commodore 64, where the official PLA IC tends to go bad over time. Due to the complexity of the logic in these PLA ICs, here CPLDs are used, which internally are still EEPROM-based, but feature many more programmable elements to allow for more complex logic. If all you need is a bit of glue logic and you are looking for something in between a stack of 74-logic ICs and a CPLD, an EEPROM may be just be the solution, regardless of whether you prefer to create the binary image with Lisp or C.
Continue reading “Using EPROMS And EEPROMs As Programmable Logic With Lisp”