You know things are getting real when the Dremel is one of the first tools you turn to after unboxing your new oscilloscope. But when your goal is to hack the scope to play Breakout, sometimes plastic needs to be sacrificed.
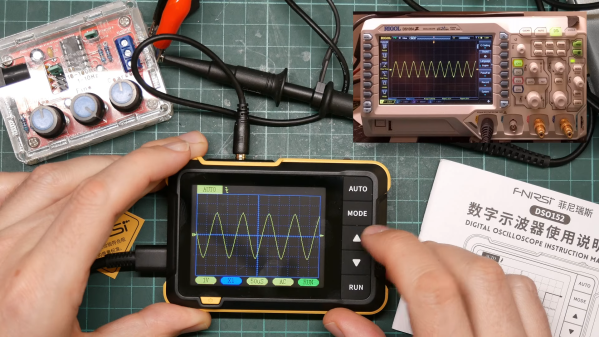
Granted, the scope in question, a Fnirsi DSO152, only cost [David Given] from Poking Technology a couple of bucks. And while the little instrument really isn’t that bad inside, it’s limited to a single channel and 200 kHz of bandwidth, so it’s not exactly lab quality. The big attractions for [David] were the CH32F103 microcontroller and the prominent debug port inside, not to mention the large color LCD panel.
[David]’s attack began with the debug port and case mods to allow access, but quickly ground to a halt when he accidentally erased the original firmware. But no matter — tracing out the pins is always an option. [David] made that easier by overlaying large photos of both sides of the board, which let him figure out which buttons went to which pins, and mapping for the display’s parallel interface. He didn’t mess with any of the analog stuff except to create a quick “Hello, oscilloscope!” program to output a square wave to the calibration pin. He did, however, create a display driver and port a game of breakout to the scope — video after the hop.
We’ve been seeing a lot of buzz around the CH32xx MCUs lately; seeing it start to show up in retail products is perhaps a leading indicator of where the cheap RISC chips are headed. We’ve seen a few interesting hacks with them, but we’ve also heard tell they can be hard to come by. Maybe getting one of these scopes to tear apart can fix that, though.
Continue reading “Hacked Oscilloscope Plays Breakout, Hints At More”