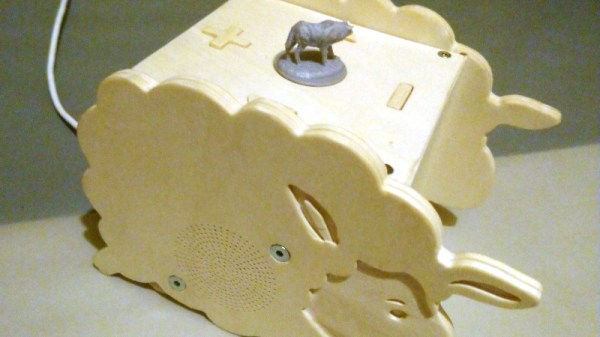
Though kids today have an incredible knack for figuring out modern phones and tablets, there’s still something to be said for offering a simple physical user interface for little hands. To that end, [Martin Hierholzer] has put together a whimsical jukebox that his two year old daughter can use to listen to her favorite songs. With just a few simple buttons, no display to read, and the ability to stop and start songs using RFID tags embedded into 3D printed figures, it’s a perfect interface for tiny humans just getting the hang of interacting with technology.
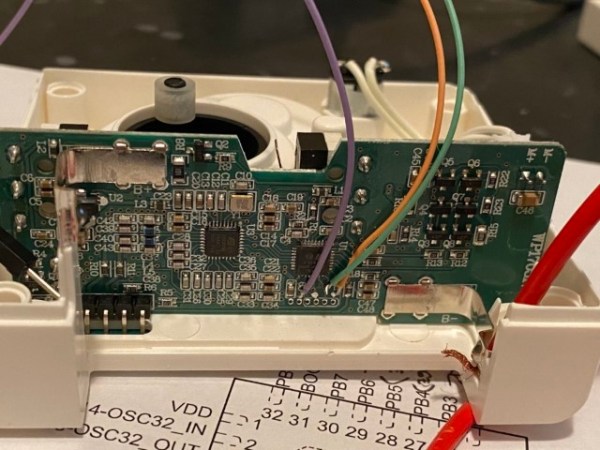
While the Raspberry Pi might have been the more obvious choice to base this project around, [Martin] decided to go the ESP32 route for improved energy efficiency. The popular microcontroller is more than powerful enough to play MP3s, and its integrated WiFi connectivity allows the player to download new tracks from the network occasionally. He added a micro SD slot to provide some mass storage, a PCM5102 I2S DAC with a PAM8403 amplifier to handle the audio side of things, and a MFRC522 RFID receiver that can pick up tags placed on the top of the player. Power is provided by parts salvaged from a USB battery bank, and everything is housed on a custom PCB.
The relatively low power requirements of the ESP32 means the jukebox can keep the party going for many hours (perhaps even days) when in active use. When the RFID token is removed and there are no songs to play, some clever coding kicks the chip into low-power mode to greatly extend the player’s standby time. [Martin] says it can sleep for months without having to be recharged, and considering some of the impressive feats of battery-sipping we’ve previously seen from the ESP32, we don’t doubt it.
Even if you don’t have any young music lovers at home, the documentation [Martin] has put together for this project is absolutely worth a look. Whether its how he configures the server side to push songs and firmware updates to the player, how he wrangled the ESP32’s Ultra-Low Power coprocessor (ULP), or the woodworking tips used to produce the charming enclosure, you’re sure to pick up a trick or two.
The children of hackers and makers always seem to get the coolest stuff, and we’re looking forward to seeing what [Martin] comes up with next. After all, kids grow up fast and pretty soon his daughter is going to need something new to entertain her.