There are plenty of stories floating around about the war in Ukraine, and it can be difficult to sort out which ones are fact-based, and which are fabrications. Stories about the technology of the war seem to be a little easier to judge, and so stories about an inside look at a purported Russian drone reveal a lot of interesting technical details. The fixed-wing UAV, reported to be a Russian-made “Orlan,” looks quite the worse for wear as it’s given a good teardown by someone wearing Ukraine military fatigues. In fact, it looks downright homemade, with a fuel tank made from what looks like an old water bottle, liberal use of duct tape to hold things together, and plenty of hot glue sprinkled around — field-expedient repairs, perhaps? The big find, though, is that the surveillance drone carried a rather commonplace — and cheap — Canon EOS Rebel camera. What’s more, the camera is nestled into a 3D printed cradle, strapped in with some hook-and-loop tape, and its controls are staked in place with globs of glue. It’s an interesting collection of hardware for a vehicle said to cost the Russian military something like $100,000 to field. The video below shows a teardown of a different Orlan with similar results, plus a lot of dunking on the Russians by a cheery bunch of Ukrainians.
ukraine13 Articles
Helping The War Effort With 3D Printed Tourniquets
It’s a sad statement on the modern world that even civilians are at risk for severe traumatic injuries in the course of going about their lives. And if something unthinkable happens to you or someone you love, here’s hoping both that the injury can be treated, and that someone is nearby who both knows what to do and is properly equipped to do it.
That’s the thinking behind these 3D printed tourniquets, an unfortunate but necessary response to the ongoing war in Ukraine. To get tourniquets into the hands of those trained to use them, [3DPrintingforUkraine] is working on plans for a printable version of the C-A-T, or combat application tourniquet, a lightweight but strong tourniquet that can be rapidly applied, even by victims themselves. The commercial device consists of molded nylon buckles and hook-and-loop fastener bands, along with a very sturdy plastic handle that serves as a windlass that provides the necessary occlusive force when twisted. The 3D printed version’s parts aren’t as streamlined as the commercial unit’s, but they appear to be strong enough to withstand the considerable forces involved. From the look of their site, STL files and instructions for assembly will be available soon.
To be clear, tourniquets should only be applied by someone properly trained to do so. But having ample tourniquets available where traumatic injuries to the extremities are likely to occur can only improve the odds that one will be available when it’s needed. So hats off to [3DPrintingforUkraine] for making the effort to push this forward.
[Austin Everman] sent us this tip. Thanks!
Hackaday Links: March 13, 2022
As Russia’s war on Ukraine drags on, its knock-on effects are being felt far beyond the eastern Europe theater. And perhaps nowhere is this more acutely felt than in the space launch industry, seeing that at least until recently, Russia was pretty much everyone’s go-to ride to orbit. All that has changed now, at least temporarily, and has expanded to include halting sales of rocket engines used in other nations’ launch vehicles. Specifically, Roscosmos has put an end to exports of the RD-180 engine used in the US Atlas V launch vehicle, along with the RD-181 thrusters found in the Antares rocket. The loss of these engines may be more symbolic than practical, at least for the RD-180 — United Launch Alliance stopped selling launches on Atlas V back last year, and had secured the engines it needed for the 29 flights it has booked by that April. Still, there’s some irony that the Atlas V, which started life as an ICBM aimed at the USSR in the 1950s, has lost its Russian-made engines.
Bad news for Jan Mrázek’s popular open-source parametric search utility which made JLCPCB’s component library easier to use. We wrote about it back in 2020, and things seemed to be going fine up until this week, when Jan got a take-down request for his service. When we first heard about this, we checked the application’s web page, which bore a big red banner that included what were apparently unpleasant accusations Jan had received, including the words “reptile” and “parasitic.” The banner is still there, but the text has changed to a more hopeful tone, noting that LCSC, the component supplier for JLC’s assembly service, objected to the way Jan was pulling component data, and that they are now working together on something that everyone can be happy with. Here’s hoping that the service is back in action again soon.
Good news, everyone: Epson is getting into the 3D printer business. Eager to add a dimension to the planar printing world they’ve mostly worked in, they’ve announced that they’ll be launching a direct-extrusion printer sometime soon. Aimed at the industrial market, the printer will use a “flat screw extruder,” which is supposed to be similar to what the company uses on its injection molding machines. We sure didn’t know Epson was in the injection molding market, so it’ll be interesting to see if expertise there results in innovation in 3D printing, especially if it trickles down to the consumer printing market. Just as long as they don’t try to DRM the pellets, of course.
You can’t judge a book by its cover, but it turns out that there’s a lot you can tell about a person’s genetics just by looking at their face. At least that’s according to an AI startup called FDNA, which makes an app called “Face2Gene” that the company claims can identify 300 genetic disorders by analyzing photos of someone’s face. Some genetic disorders, like Down Syndrome, leave easily recognizable facial features, but some changes are far more subtle and hard to recognize. We had heard of cases where photos of toddlers posted on social media were used to diagnose retinoblastoma, a rare cancer of the retina. But this is on another level entirely.
And finally, working in an Amazon warehouse has got to be a tough gig, and if some of the stories are to be believed, it borders on being a horror show. But one Amazonian recently shared a video that showed what it’s like to get trapped by his robotic coworkers. The warehouse employee somehow managed to get stuck in a maze created by Amazon’s pods, which are stacks of shelves that hold merchandise and are moved around the warehouse floor by what amounts to robotic pallet jacks. Apparently, the robots know enough to not collide with their meat-based colleagues, but not enough to not box them in. To be fair, the human eventually found a way out, but it was a long search and it seems like another pod could have moved into position to block the exit at any time. You could see it as a scary example of human-robot interaction gone awry, but we prefer to look at it as the robots giving their friend a little unscheduled break away from the prying eyes of his supervisor.
The Invisible Battlefields Of The Russia-Ukraine War
Early in the morning of February 24th, Dr. Jeffrey Lewis, a professor at California’s Middlebury Institute of International Studies watched Russia’s invasion of Ukraine unfold in realtime with troop movements overlaid atop high-resolution satellite imagery. This wasn’t privileged information — anybody with an internet connection could access it, if they knew where to look. He was watching a traffic jam on Google Maps slowly inch towards and across the Russia-Ukraine border.
As he watched the invasion begin along with the rest of the world, another, less-visible facet of the emerging war was beginning to unfold on an ill-defined online battlefield. Digital espionage, social media and online surveillance have become indispensable instruments in the tool chest of a modern army, and both sides of the conflict have been putting these tools to use. Combined with civilian access to information unlike the world has ever seen before, this promises to be a war like no other.
Modern Cyberwarfare
The first casualties in the online component of the war have been websites. Two weeks ago, before the invasion began en masse, Russian cyberwarfare agents launched distributed denial of service (DDoS) attacks against Ukrainian government and financial websites. Subsequent attacks have temporarily downed the websites of Ukraine’s Security Service, Ministry of Foreign Affairs, and government. A DDoS attack is a relatively straightforward way to quickly take a server offline. A network of internet-connected devices, either owned by the aggressor or infected with malware, floods a target with request, as if millions of users hit “refresh” on the same website at the same time, repeatedly. The goal is to overwhelm the server such that it isn’t able to keep up and stops replying to legitimate requests, like a user trying to access a website. Russia denied involvement with the attacks, but US and UK intelligence services have evidence they believe implicates Moscow. Continue reading “The Invisible Battlefields Of The Russia-Ukraine War”
Hackaday Links: March 6, 2022
As if the war in Ukraine weren’t bad enough right here on Earth, it threatens knock-on effects that could be felt as far away as Mars. One victim of the deteriorating relationships between nations is the next phase of the ExoMars project, a joint ESA-Roscosmos mission that includes the Rosalind Franklin rover. The long-delayed mission was most recently set for launch in October 2022, but the ESA says that hitting the narrow launch window is now “very unlikely.” That’s a shame, since the orbital dynamics of Earth and Mars will mean that it’ll be 2024 before another Hohmann Transfer window opens. There are also going to be repercussions throughout the launch industry due to Russia pulling the Soyuz launch team out of the ESA’s spaceport in Guiana. And things have to be mighty tense aboard the ISS right about now, since the station requires periodic orbital boosting with Russian Progress rockets.
This Week In Security: Ukraine, Nvidia, And Conti
The geopolitics surrounding the invasion of Ukraine are outside the scope of this column, but the cybersecurity ramifications are certainly fitting fodder. The challenge here is that almost everything of note that has happened in the last week has been initially linked to the conflict, but in several cases, the reported link hasn’t withstood scrutiny. We do know that the Vice Prime Minister of Ukraine put out a call on Twitter for “cyber specialists” to go after a list of Russian businesses and state agencies. Many of the sites on the list did go down for some time, the digital equivalent of tearing down a poster. In response, the largest Russian ISP stopped announcing BGP routes to some of the targeted sites, effectively ending any attacks against them from the outside.
A smattering of similar events have unfolded over the last week, like electric car charging stations in Russia refusing to charge, and displaying a political message, “GLORY TO UKRAINE”. Not all the attacks have been so trivial. Researchers at Eset have identified HermeticWiper, a bit of malware with no other purpose but to destroy data. It has been found on hundreds of high-value targets, likely causing much damage. It is likely the same malware that Microsoft has dubbed FoxBlade, and published details about their response. Continue reading “This Week In Security: Ukraine, Nvidia, And Conti”
The Battlefield That’s 5 KHz Wide
The airwaves are full of news from the battle in Ukraine, with TV and radio journalists providing coverage at all hours. But for those with a bit of patience there’s something else from the conflict that can be found with a radio receiver, the battle over 5 kHz of spectrum starting at 4625 kHz. This has for many years been the location on the dial for “the Buzzer“, a Russian military transmitter whose nickname describes its monotonous on/off buzzing transmission perfectly. As the current Ukrainian situation has taken shape it has become a minor battleground, and the Buzzer now shares its frequency with a variety of other stations broadcasting music, spectrograms, and other radio junk intended to disrupt it.
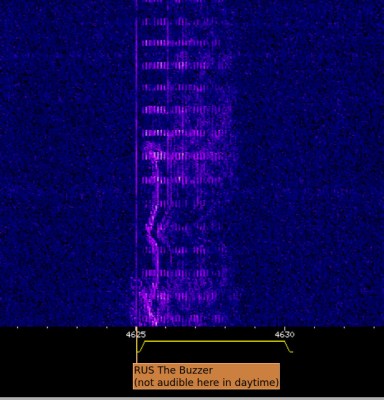
For the curious this can be watched unfolding on a spectrogram or through headphones by anyone within range who has an HF receiver, or for everyone else, with a WebSDR. In Western Europe it’s best listened to in hours of darkness, we suggest you consult the webSDR.org list to see which has the best signal. We’ve heard it on receivers in Poland, Russia, and the ever-reliable uTwente WebSDR in the Netherlands. Over the time we’ve been monitoring it we’ve heard overlaying speech, and music varying from the Soviet and American anthems through dance music and K-pop to 1960s British rock and of course Boney M’s Rasputin, with a few slightly macabre choices such as Final Countdown and an air raid siren. We’ve even heard TV intros from the Benny Hill Show, the A-Team and Mission Impossible, so whoever is doing this has a wide taste.
Alongside the music at about 4628kHz meanwhile we’ve watched a series of spectrogram messages scroll past in Ukrainian, Russian, and English, ranging from “Stop war” to lewd suggestions about the Russian President. It’s fair to say that none of these transmissions have obscured the Buzzer, but they have had the effect of significantly increasing the noise on the channel.
To have a listen yourself, point a receiver within range at the appropriate time of day towards 4625 kHz and select USB demodulation and a 5 kHz bandwidth. Meanwhile, for some background on the Cold War HF relics, have a read about numbers stations.
















