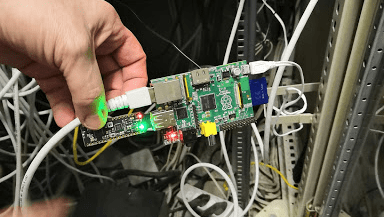
When one of [Christian Haschek’s] co-workers found this Raspberry Pi tucked into their network closet, he figured it was another employee’s experiment – you know how that goes. But, of course, they did the safe thing and unplugged it from the network right away. The ensuing investigation into what it was doing there is a tour de force in digital forensics and a profile of a bungling adversary.
A quick check of everyone with access to that area turned up nothing, so [Christian] shifted focus to the device itself. There were three components: a Raspberry Pi model B, a 16GB SD card, and an odd USB dongle that turned out to be an nRF52832-MDK. The powerful SoC on-board combines a Cortex M4 processor with the RF hardware for BLE, ANT, and other 2.4 GHz communications. In this case, it may have been used for sniffing WiFi or bluetooth packets.
The next step was investigating an image of the SD card, which turned out to be a resin install (now called balena). This is an IoT web service that allows you to collect data from your devices remotely via a secure VPN. Digging deeper, [Christian] found a JSON config file containing a resin username. A little googling provided the address of a nearby person with the same name – but this could just be coincidence. More investigation revealed a copyright notice on some mysterious proprietary software installed on the Pi. The copyright holder? A company part-owned by the same person. Finally, [Christian] looked into a file called resin-wifi-01 and found the SSID that was used to set up the device. Searching this SSID on wigle.net turned up – you guessed it – the same home address found from the username.
But, how did this device get there in the first place? Checking DNS and Radius logs, [Christian] found evidence that an ex-employee with a key may have been in the building when the Pi was first seen on the network. With this evidence in hand, [Christian] turned the issue over to legal, who will now have plenty of ammunition to pursue the case.
If you find the opportunity to do some Linux forensics yourself, or are simply interested in learning more about it, this intro by [Bryan Cockfield] will get you started.