Do you want to be a better person? Maybe you want to curse less, drink more water, or post fewer inflammatory comments on the internet. You could go the old school route by wearing a rubber band around your wrist and snapping it every time you slip, or literally pat yourself on the back when you do the right thing. While these types of reinforcement methods may deter bad behavior and encourage good, they are quite lean on data. And who wants that?
After an unpleasant conference call, [Darian] cursed a blue streak that left his coworkers shocked and speechless. This inciting incident began the hero’s journey that will end with a kinder, gentler [Darian], as long as he has his trusty Be Better Bracelet. He tried involving Alexa when at home, and various apps elsewhere to track these venomous utterances, but he yearned for a single solution that’s always available.
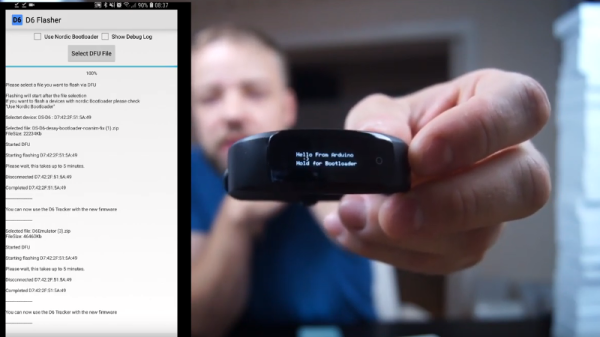
The sole purpose of this bracelet is low-cost, unobtrusive habit tracking. Though tied to a phone, it won’t tell time, predict the weather, or alert the user to incoming what-have-yous. It will simply record button presses, which are assigned meaning in the app settings. It’s up to the user to set goals, analyze the data, and reward or punish themselves accordingly.
[Darian] is still working out the design kinks to make this as small and cheap as possible. If you have suggestions, let him know.