Leading edge computer security is veiled in secrecy — a world where novel attacks are sprung on those who do not yet know what they need to protect against. Once certain tactics have played out within cool kids’ circles, they are introduced to the rest of the world. An IBM red team presented what they’re calling “warshipping”: sending an adversarial network to you in a box.
Companies concerned about security have learned to protect their internet-accessible points of entry. Patrolling guards know to look for potential wardrivers parked near or repeatedly circling the grounds. But some are comparatively lax about their shipping & receiving, and they are the ideal targets for warshipping.
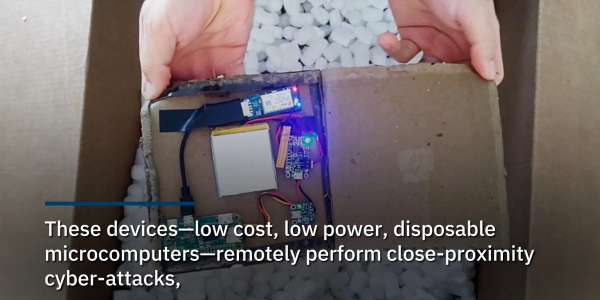
Bypassing internet firewalls and security perimeters, attack hardware is embedded inside a shipping box and delivered by any of the common carriers. Security guards may hassle a van bristling with antennas, but they’ll wave a FedEx truck right through! The hardware can be programmed to stay dormant through screening, waiting to probe once inside the walls.
The presentation described several ways to implement such an attack. There is nothing novel about the raw hardware – Raspberry Pi, GPS receiver, cellular modems, and such are standard fare for various projects on these pages. The creative part is the software and in how they are hidden: in packing material and in innocuous looking plush toys. Or for persistence, they can be hidden in a wall mounted plaque alongside some discreet photovoltaic panels. (Editor’s note: What? No Great Seals?)
With this particular technique out in the open, we’re sure others are already in use and will be disclosed some years down the line. In the meantime, we can focus our efforts on more benign applications of similar technology, whether it is spying on our cat or finding the nearest fast food joint. The hardware is evolving as well: a Raspberry Pi actually seems rather heavyweight for this, how about a compact PCB with both an ESP32 and a cellular modem?
Via Ars Technica.