Nintendo look as though they may have something of a hit on their hands with their latest console offering. It’s not the next in the line of high-end consoles with immersive VR or silicon that wouldn’t have looked out of place in last year’s supercomputer, instead it’s an homage to one of their past greats. The NES Classic Edition is a reboot of the 1980s console with the familiar styling albeit a bit smaller, and 30 of the best NES games included.
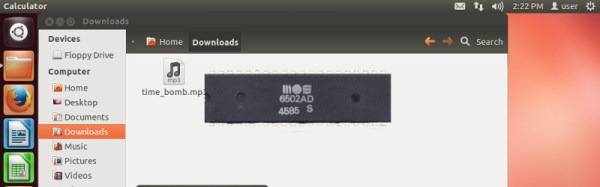
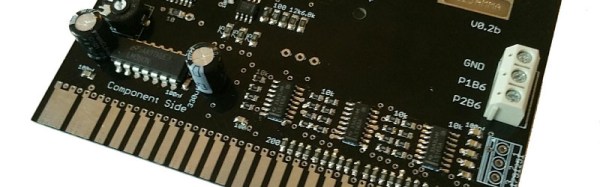
You do not, however, get an original NES with a 6502 derived processor, and a stack of game cartridges. In the Classic Edition is a modern emulator, running on very modern hardware. We’re told it contains an Allwinner R16 quad-core Cortex A7 SoC, 256Mb of RAM, and 512Mb of Flash. That’s a capable system, and unsurprisingly any hacking potential it may have has attracted some interest. Reddit user [freenesclassic] for example has been investigating its potential as a Linux machine, and has put up a post showing the progress so far. It is known that there is already some form of Linux underpinning the console because Nintendo have released a set of sources as part of their compliance with the terms of the relevant open-source licences. That and the availability of a serial port via pads on the PCB gives hope that a more open distro can be installed on it.
We’re taken through the process of starting the machine up with the serial port connected to a PC, and getting it into the Allwinner FEL mode for low-level flashing work. Then we’re shown the process of loading a custom U-Boot, from which in theory a kernel of your choice can be loaded.
Of course, it’s not quite that simple. There is still some way to go before the device’s Flash can be accessed so for now, all that is possible is to use the RAM, and the current state of play has a kernel panic as it is unable to mount a filesystem. However this is a new piece of hardware in its first few days after launch, so this is very much a work in progress. We are sure that this device will in time be opened up as a fully hackable piece of hardware, and we look forward to covering the interesting things people do with it when that has happened.
If you are interested in the NES Classic, take a look at it on Nintendo’s web site. Meanwhile, here at Hackaday as a quick look at our past stories tagged “nes” shows, we’ve covered a huge number of projects involving the platform in the past.
Thanks [Doc Oct] for the tip.
Original NES console header image: Evan-Amos [Public domain], via Wikimedia Commons.
![A GPIB/IEEE488 plug. Alkamid [CC BY-SA 3.], via Wikimedia Commons](https://hackaday.com/wp-content/uploads/2016/10/a_gpib_plug.jpg?w=400)