Quick, what’s 360 divided by 23? It’s easy enough to get the answer, of course, but if you need to machine a feature every 15.652 degrees around a shaft, how exactly would you accomplish that? There are a number of ways, but they all involve some degree of machining wizardry. Or, you can just make the problem go away with a little automation.
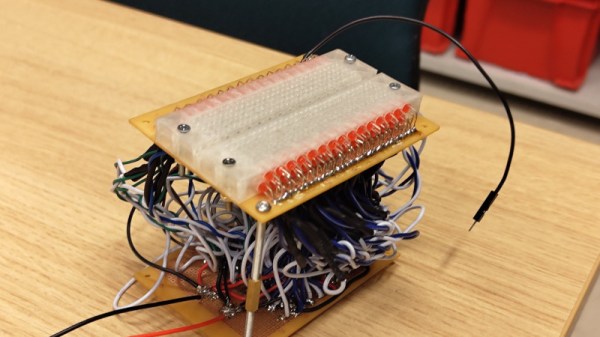
The story behind [Tony Goacher]’s Rotary Table Buddy begins with some ATV tracks he got off AliExpress. His idea is to build a specialty electric vehicle for next year’s EMF Camp. The tracks require a splined shaft to drive them, which would need to be custom-made on a milling machine. A rotary table with a dividing plate — not as fancy as this one, of course –is usually the answer, but [Tony] was a little worried about getting everything set up correctly, so he embarked on a tactical automation solution to the problem.
An RP2040 provided the brains of the project, while a NEMA 23 stepper provides the brawn. [Tony] whipped up a quick PCB and 3D printed a case for the microcontroller, a stepper driver, an LCD display, and a few buttons. He 3D printed an adapter and a shaft coupler to mount the stepper motor to a rotary table. From there it was just a matter of coming up with a bit of code to run everything.
There’s a brief video in [Tony]’s blog post that shows Rotary Table Buddy in action, indexing to the next position after cutting one of the 23 splines. He says it took about ten minutes to cut each spline using this setup, which probably makes to total cutting time far less than the amount of time invested in the tool. But that’s hardly the point, and besides, now he’s set up for all kinds of machining operations in the future.
And we sure hope we hear about the EMF Camp build, too.