Most people would recognize E.T. The Extra-Terrestrial for the Atari 2600 by its reputation as one of the worst video games of all time. We’ll have more to say about that in a moment, but E.T. was nevertheless chosen as the inspiration behind [Martin Fitzpatrick]’s re-imagining of the game in ten lines of BASIC code for a contest that encourages and celebrates games written in ten lines of BASIC, or less.
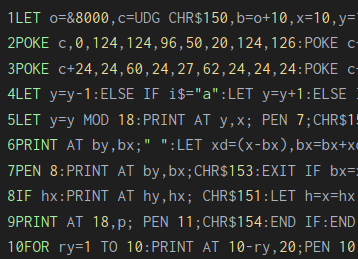 Ten lines of BASIC is a big limitation, even when getting clever by stacking multiple statements into a single line, so [Martin]’s game has a much narrower scope than the original Atari 2600 version. Still, the core elements are present: E.T. must find and gather all the parts of the phone in order to contact his ship, after which he must meet the ship in time to escape. All the while, FBI agents attempt to interfere. The game was written in SAM BASIC, used by the SAM Coupé, a British Z80-based home computer from the late 80s with an emulator available for download.
Ten lines of BASIC is a big limitation, even when getting clever by stacking multiple statements into a single line, so [Martin]’s game has a much narrower scope than the original Atari 2600 version. Still, the core elements are present: E.T. must find and gather all the parts of the phone in order to contact his ship, after which he must meet the ship in time to escape. All the while, FBI agents attempt to interfere. The game was written in SAM BASIC, used by the SAM Coupé, a British Z80-based home computer from the late 80s with an emulator available for download.
Now, for lovers of “um, actually” topics, do we have a treat for you! Let’s take this opportunity to review a few things about E.T. The Extra-Terrestrial. That it was a commercial flop is no doubt, but the game itself is often badly misunderstood. Way back in 2013 we covered an extraordinary effort to patch improvements into the binary for the 2600 game, and in the process there’s a compelling case made that the game was in many ways far ahead of its time, and actually quite significant in terms of game design. You can jump right in on an analysis of the hate the game receives, and while reading that it’s helpful to keep in mind that In 1982, many of its peers were games like Space Invaders, with self-evident gameplay that simply looped endlessly.