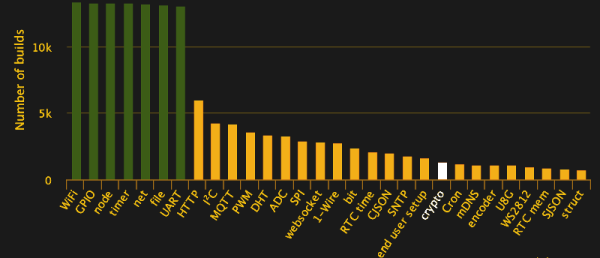
When the ESP-8266 first arrived, it was a marvel. For two dollars, you could buy a simple module that could serve as a bridge between WiFi networks and microcontroller projects. It understood the Hayes command set, it didn’t use much power, and, as noted before, it only cost two dollars. The idea of cheap and accessible Internet of Things things was right there for the taking.
 Then hackers figured out what was actually going on inside the ESP-8266. It was a full-blown microcontroller. There was Lua stuff you could put on it. You could program it with the Arduino IDE. It had WiFi. This was the greatest microcontroller release in the last decade, and it came from a company no one had ever heard of.
Then hackers figured out what was actually going on inside the ESP-8266. It was a full-blown microcontroller. There was Lua stuff you could put on it. You could program it with the Arduino IDE. It had WiFi. This was the greatest microcontroller release in the last decade, and it came from a company no one had ever heard of.
Since then, the ESP ecosystem has bloomed, and there’s a new ESP on the block. The ESP-32 is an even more powerful WiFi and Bluetooth-enabled chip that’s just as easy to program, and it costs three dollars. Microcontrollers have never been cooler.
For this week’s Hack Chat, we’re going to be talking all about the ESP. Our guest for this Hack Chat should need no introduction, but if you’re unfamiliar, [Sprite_tm] plays video games on his keyboard and has installed Linux on a hard drive. He also works at Espressif, the company behind the ESP-8266 and ESP-32, where he’s applied his skills towards tiny Game Boys and miniature Macs.
During this week’s Hack Chat, we’re going to be covering everything about the ESP, including peripherals, ultra-low power consumption, SIP packages, and what’s coming up for the ESP family. You are, as always, welcome to submit your questions for [Sprite]; just add those as a comment on the Hack Chat page.
Our Hack Chats are live community events on the Hackaday.io Hack Chat group messaging. [Sprite]’s in China, so we’re not doing this one at the usual time: This week, the Hack Chat will happen at 7:00 am, Pacific, Friday, March 9th. Want to know what time this is happening in your neck of the woods? Have a countdown timer!
Click that speech bubble to the right, and you’ll be taken directly to the Hack Chat group on Hackaday.io.
You don’t have to wait until Friday; join whenever you want and you can see what the community is talking about.