In the dark ages, before iOS and Android phones became ubiquitous, there was the PDA. These handheld computers acted as simple companions to a computer and could often handle calendars, email, notes and more. Their demise was spelled by the smartphone, but the nostalgia of having a simple handheld and romanticizing about the 90’s and 2000’s is still there. Fortunately for the nostalgic among our readers, [Ashtf] decided to give us a modern take on the classic PDAs.
DIY Record Cutting Lathe Is Really Groovy
Back in the day, one of the few reasons to prefer compact cassette tape to vinyl was the fact you could record it at home in very good fidelity. Sure, if you had the scratch, you could go out and get a small batch of records made from that tape, but the machinery to do it was expensive and not always easy to come by, depending where you lived. That goes double today, but we’re in the middle of a vinyl renaissance! [ronald] wanted to make records, but was unable to find a lathe, so decided to take matters into his own hands, and build his own vinyl record cutting lathe.
![photograph of [ronald's] setup](https://hackaday.com/wp-content/uploads/2025/04/groovy_lathe.png?w=301)
British Wartime Periscope: A Peek Into The Past
We all know periscopes serve for observation where there’s no direct line-of-sight, but did you know they can allow you to peer through history? That’s what [msylvain59] documented when he picked up a British military night vision periscope, snagged from a German surplus shop for just 49 euros. Despite its Cold War vintage and questionable condition, the unit begged for a teardown.
The periscope is a 15-kilo beast: industrial metal, cryptic shutter controls, and twin optics that haven’t seen action since flares were fashionable. One photo amplifier tube flickers to greenish life, the other’s deader than a disco ball in 1993. With no documentation, unclear symbols, and adjustment dials from hell, the teardown feels more like deciphering a British MoD fever dream than a Sunday project. And of course, everything’s imperial.
Despite corrosion, mysterious bulbs, and non-functional shutters, [msylvian59] uncovers a fascinating mix of precision engineering and Cold War paranoia. There’s a thrill in tracing light paths through mil-spec lenses (the number of graticules seen that are etched on the optics) and wondering what secrets they once guarded. This relic might not see well anymore, but it sure makes us look deeper. Let us know your thoughts in the comments or share your unusual wartime relics below.
Continue reading “British Wartime Periscope: A Peek Into The Past”
Game Boy PCB Assembled With Low-Cost Tools
As computers have gotten smaller and less expensive over the years, so have their components. While many of us got our start in the age of through-hole PCBs, this size reduction has led to more and more projects that need the use of surface-mount components and their unique set of tools. These tools tend to be more elaborate than what would be needed for through-hole construction but [Tobi] has a new project that goes into some details about how to build surface-mount projects without breaking the bank.
The project here is interesting in its own right, too: a display module upgrade for the classic Game Boy based on an RP2350B microprocessor. To get all of the components onto a PCB that actually fits into the original case, though, surface-mount is required. For that [Tobi] is using a small USB-powered hotplate to reflow the solder, a Pinecil, and a healthy amount of flux. The hotplate is good enough for a small PCB like this, and any solder bridges can be quickly cleaned up with some extra flux and a quick pass with a soldering iron.
The build goes into a lot of detail about how a process like this works, so if you’ve been hesitant to start working with surface mount components this might be a good introduction. Not only that, but we also appreciate the restoration of the retro video game handheld complete with some new features that doesn’t disturb the original look of the console. One of the other benefits of using the RP2350 for this build is that it’s a lot simpler than using an FPGA, but there are perks to taking the more complicated route as well.
Continue reading “Game Boy PCB Assembled With Low-Cost Tools”
Why Physical Media Deserved To Die
Over the course of more than a decade, physical media has gradually vanished from public view. Once computers had an optical drive except for ultrabooks, but these days computer cases that even support an internal optical drive are rare. Rather than manuals and drivers included on a data CD you now get a QR code for an online download. In the home, DVD and Blu-ray (BD) players have given way to smart TVs with integrated content streaming apps for various services. Music and kin are enjoyed via smart speakers and smart phones that stream audio content from online services. Even books are now commonly read on screens rather than printed on paper.
With these changes, stores selling physical media have mostly shuttered, with much audiovisual and software content no longer pressed on discs or printed. This situation might lead one to believe that the end of physical media is nigh, but the contradiction here comes in the form of a strong revival of primarily what used to be considered firmly obsolete physical media formats. While CD, DVD and BD sales are plummeting off a cliff, vinyl records, cassette tapes and even media like 8-track tapes are undergoing a resurgence, in a process that feels hard to explain.
How big is this revival, truly? Are people tired of digital restrictions management (DRM), high service fees and/or content in their playlists getting vanished or altered? Perhaps it is out of a sense of (faux) nostalgia?
What’s Sixty Feet Across And Superconducting?
What’s sixty feet (18.29 meters for the rest of the world) across and superconducting? The International Thermonuclear Experimental Reactor (ITER), and probably not much else.
The last parts of the central solenoid assembly have finally made their way to France from the United States, making both a milestone in the slow development of the world’s largest tokamak, and a reminder that despite the current international turmoil, we really can work together, even if we can’t agree on the units to do it in.
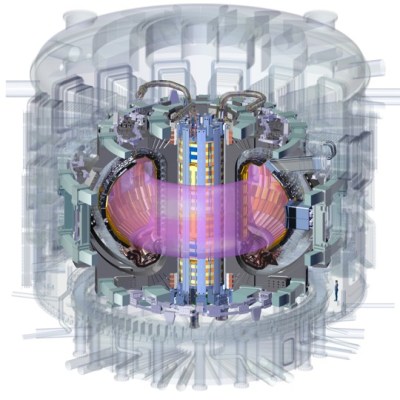
The central solenoid is 4.13 m across (that’s 13′ 7″ for burger enthusiasts) sits at the hole of the “doughnut” of the toroidal reactor. It is made up of six modules, each weighing 110 t (the weight of 44 Ford F-150 pickup trucks), stacked to a total height of 59 ft (that’s 18 m, if you prefer). Four of the six modules have been installed on-site, and the other two will be in place by the end of this year.
Each module was produced ITER by US, using superconducting material produced by ITER Japan, before being shipped for installation at the main ITER site in France — all to build a reactor based on a design from the Soviet Union. It doesn’t get much more international than this!
This magnet is, well, central to the functioning of a tokamak. Indeed, the presence of a central solenoid is one of the defining features of this type, compared to other toroidal rectors (like the earlier stellarator or spheromak). The central solenoid provides a strong magnetic field (in ITER, 13.1 T) that is key to confining and stabilizing the plasma in a tokamak, and inducing the 15 MA current that keeps the plasma going.
When it is eventually finished (now scheduled for initial operations in 2035) ITER aims to produce 500 MW of thermal power from 50 MW of input heating power via a deuterium-tritium fusion reaction. You can follow all news about the project here.
While a tokamak isn’t likely something you can hack together in your back yard, there’s always the Farnsworth Fusor, which you can even built to fit on your desk.
Making A One-Of-A-Kind Lime2 SBC
Upgrading RAM on most computers is often quite a straightforward task: look up the supported modules, purchase them, push a couple of levers, remove the old, and install the new. However, this project submitted by [Mads Chr. Olesen] is anything but a simple.
In this project, he sets out to double the RAM on a Olimex A20-OLinuXino-LIME2 single-board computer. The Lime2 came with 1 GB of RAM soldered to the board, but he knew the A20 processor could support more and wondered if simply swapping RAM chips could double the capacity. He documents the process of selecting the candidate RAM chip for the swap and walks us through how U-Boot determines the amount of memory present in the system.
While your desktop likely has RAM on removable sticks, the RAM here is soldered to the board. Swapping the chip required learning a new skill: BGA soldering, a non-trivial technique to master. Initially, the soldering didn’t go as planned, requiring extra steps to resolve issues. After reworking the soldering, he successfully installed both new chips. The moment of truth arrived—he booted up the LIME2, and it worked! He now owns the only LIME2 with 2 GB of RAM.
Be sure to check out some other BGA soldering projects we’ve featured over the years.

















