The Internet of Things is going gangbusters, despite no one knowing exactly what it will be used for. There’s more marketing money being thrown at IoT paraphernalia than a new soda from Pepsi. It’s a new technology, and with that comes a few problems: these devices are incredibly insecure, and you only need to look at a few CCTV camera streams available online for proof of that.
The obvious solution to vulnerable Internet of Things things would be to get people to change the login credentials on their devices, but that has proven to be too difficult for most of the population. A better solution, if questionable in its intentions, would be a virus that would close all those open ports on routers, killing Telnet, and reminding users to change their passwords. Symantec has found such a virus. It’s called Wifatch, and it bends the concept of malware into a force for good.
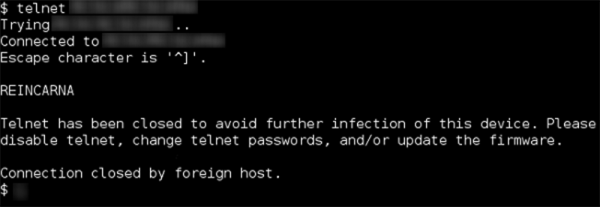
Wifatch is a bit of code that slips through the back door of routers and other IoT devices, closes off Telnet to prevent further infection, and leaves a message telling the owner to change the password and update the device firmware. Wifatch isn’t keeping any secrets, either: most of the code is written in unobfuscated Perl, and there are debug messages that enable easy analysis of the code. This is code that’s meant to be taken apart, and code that includes a comment directed at NSA and FBI agents:
To any NSA and FBI agents reading this: please consider whether defending the US Constitution against all enemies, foreign or domestic, requires you to follow Snowden's example.
Although the designer of Wifatch left all the code out in the open, and is arguably doing good, there is a possible dark side to this white hat virus. Wifatch connects to a peer-to-peer network that is used to distribute threat updates. With backdoors in the code, the author of Wifatch could conceivably turn the entire network of Wifatch-infected devices into a personal botnet.
While Wifatch is easily removed from a router with a simple restart, and re-infection can be prevented by changing the default passwords, this is an interesting case of virtual vigilantism. It may not be the best way to tell people they need to change the password on their router, but it’s hard to argue with results.