Florida is a great place to live, especially around January when it’s sunny and 24 degrees outside (76F) while all of your friends from back home are dealing with scraping ice off of their windshields every morning. In the late summer, though, this pleasant tropical paradise can sometimes take a turn for the worse, because Florida is one of the handful of places that frequently see some of the worst storms on the planet: hurricanes. As a Floridian myself, perhaps I can shed some light on some of the ways that the various local governments and their residents have taken to mitigate the destruction that usually accompanies these intense tropical storms when it seems that, to outsiders, it might be considered unwise to live in such a place.
Monstrous USB Power Bank
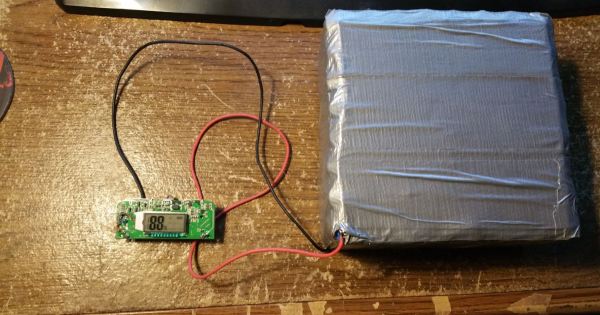
At some point, cleaning out the spare parts bin — or cabinet, or garage — becomes a necessity. This is dangerous because it can induce many more project ideas and completely negate the original purpose. [Chaotic Mind], considering the pile of batteries he’s collected over the past decade, decided that instead of throwing them out, he would recycle them into a grotesque USB power bank.
Inside the bulk of this power bank are an eye-popping 64 18650 Lithium Ion cells, mostly collected from laptop batteries, and wired in a parallel 8×8 pattern with an estimated capacity of over 100,000mAh(!!). The gatekeeper to all this stored energy is a two-USB power bank charger board from Tindie.
Ah — but how to package all this power? The handy man’s secret weapon: duct-tape!
PID Controlled Charcoal BBQ – Put An Arduino On It!
At Maker Faire Milwaukee this past weekend, [basement tech] was showing off his latest build, a PID controlled charcoal grill. While it hasn’t QUITE been tested yet with real food, it does work in theory.
PID (a feedback loop with some fancy math used to adjust the input to get a consistent output) controlled cooking is commonly used for sous vide, where one heats up a water bath to a controlled temperature to cook food in plastic bags. Maintaining water temperature is fairly easy. Controlling a charcoal barbecue is much more difficult. [basement tech] accomplishes this with controlled venting and fans. With the charcoal hot and the lid on, there are two ways to control temperature; venting to let hot air out, and blowing air on the coals to make them hotter. A thermocouple sensor stuck through the grill gives the reading of the air inside, and an Arduino nearby reads that and adjusts the vents and fans accordingly.
The video goes into extensive detail on the project, and describes some of the challenges he had along the way, such as preventing the electronics and servos from melting.
Continue reading “PID Controlled Charcoal BBQ – Put An Arduino On It!”
Smooth And Steady Cuts With An Improvised Power Feeder
Some woodworking operations require stock to be fed at a smooth, steady rate, for which purpose a power feeder is usually employed. They’re expensive bits of gear, though, and their cost can usually be borne only by high-output production shops. But when you need one, you need one, and hacking a power feeder from a drill and a skate wheel is a viable option.
It should come as no surprise that this woodshop hack comes to us from [Matthias Wandel], who never seems to let a woodworking challenge pass him by. His first two versions of expedient power feeders were tasked with making a lot of baseboard moldings in his new house. Version three, presented in the video below, allows him to feed stock diagonally across his table saw, resulting in custom cove moldings. The completed power feeder may look simple — it’s just a brushless drill in a wooden jig driving a skate wheel — but the iterative design process [Matthias] walks us through is pretty fascinating. We also appreciate the hacks within hacks that always find their way into his videos. No lathe? No problem! Improvise with a drill and a bandsaw.
Surprised that [Matthias] didn’t use some of his famous wooden gears in this build? We’re not. A brushless motor is perfect for this application, with constant torque at low speeds. Want to learn more about BLDC motors? Get the basics with a giant demo brushless motor.
Continue reading “Smooth And Steady Cuts With An Improvised Power Feeder”
The Linux FPGA
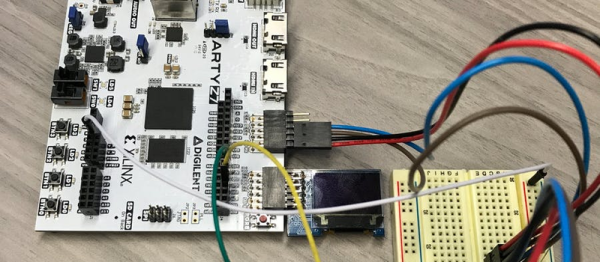
It was never unusual to have a CPU and an FPGA together. After all, each has different strengths and weaknesses. However, newer devices like the Xilinx Zynq have both a CPU and an FPGA in the same package. That means your design has to span hardware, FPGA configurations, and software. [Mitchell Orsucci] was using a Zynq device on a ArtyZ7-20 board and decided he wanted to use Linux to operate the ARM processor and provide user-space tools to interface with the FPGA and reconfigure it dynamically.
This sounds like a big project and it certainly isn’t trivial by any means. However, the Xilinx tools do a lot of the heavy lifting, including setting up the Linux kernel and a suitable root file system. The bulk of [Mitchell’s] work was in developing user space tools for Linux programs to interact with the FPGA hardware. You can see a short video demo below.
Where Can You Fly? Worldwide Drone Laws Mapped
If you are a flier of a multirotor, or drone, you should be painfully aware of the regulations surrounding them wherever you live, as well as the misinformation and sometime bizarre levels of hysteria from uninformed people over their use.
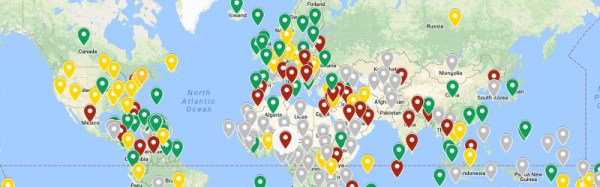
Should you travel with your drone, you will also probably be resigned to being interrogated by airport staff high on The War On Terror security theatre, and you’ll probably not find it surprising that they have little idea of the laws and regulations over which they have pulled you aside. It’s a confusing situation, and it’s one that [Anil Polat] has addressed by collating information about drone laws worldwide, and presenting his results on a Google map.
To do this must have been a huge undertaking, particularly since he got in touch with the appropriate authorities to access the information from the horse’s mouth. Looking at the map, we can almost view the green, yellow, and red pins showing different levels of restriction on flight as a fascinating indication of differing levels of security paranoia worldwide. If your territory has an orange or red pin, our commiseration.
This is a useful resource for anyone with an interest in multirotor flying, and he has also made it available as an app. However, it is always safest to check with the authorities concerned before flying in another territory, in case any laws have changed.
Here at Hackaday we’ve held an interest in the interface between multirotor fliers, governments, and the general public for a while now. In 2015 we took a look at FAA regulations for example, and last year we examined the inaccuracies in British air incident reports.
Via Adafruit.
Cheap DIY MIDI To USB Adapter
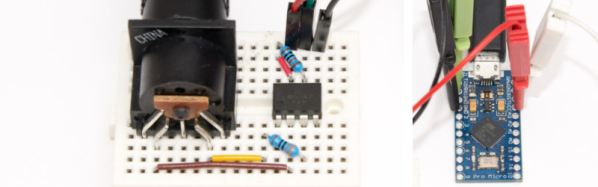
[Joonas] became frustrated with cheap but crappy MIDI to USB converters, and the better commercial ones were beyond his budget. He used a Teensy LC to build one for himself and it did the job quite well. But he needed several converters, and using the Teensy LC was going to cost him a lot more than he was willing to spend. With some tinkering, he was able to build one using an Adafruit Pro Trinket which has onboard hardware UART (but no USB). This lack of USB support was a deal killer for him, so after hunting some more he settled on a clone of the Sparkfun Pro Micro. Based on the ATmega32U4, these clones were just right for his application, and the cheapest to boot. He reckons it cost him about $5 to build each of his cheap USB MIDI adapters which receive notes and pedal data from the keyboard’s MIDI OUT and transmit them to a computer
Besides the Pro Micro clone, the only other parts he used are a generic opto-coupler, a couple of resistors and a MIDI connector. After testing his simple circuit on a bread board, he managed to squeeze it all inside an old USB dongle housing, stuffing it in dead-bug style.
The heavy lifting is all done in the firmware, for which [Joonas] used LUFA — the Lightweight USB Framework for AVR’s. He wrote his own code to handle MIDI (UART) to USB MIDI messages conversion. The interesting part is his use of a 32.15 kbps baud rate even though the MIDI specification requires 31.25 kbps. He found that a slightly higher baud rate fixes a problem in the AVR USART implementation which tends to miss consecutive bytes due to the START edge not being detected. Besides this, his code is limited in functionality to only handle a few messages, mainly for playing a piano, and does not have full-fledged MIDI capabilities.
We’ve featured several of [Joonas]’s hacks here over the years, the most recent being the Beaglebone Pin-Toggling Torture Test and from earlier, How to Turn A PC On With a Knock And An ATTiny.