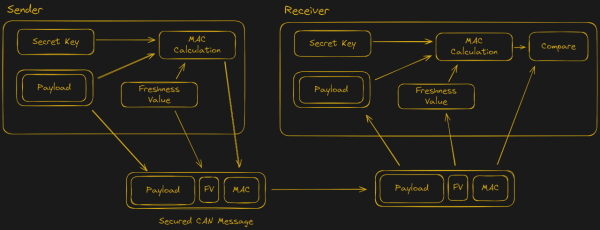
With the recently introduced SecOC (Secure Onboard Communication) standard, car manufacturers seek to make the CAN bus networks that form the backbone of modern day cars more secure. This standard adds a MAC (message authentication code) to the CAN messages, which can be used to validate that these messages come from a genuine part of the car, and not from a car thief or some third-party peripheral.
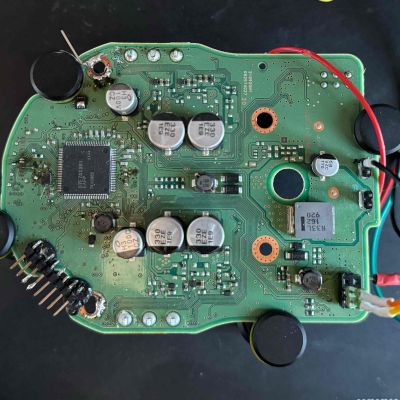
To check that it isn’t possible to circumvent SecOC, [Willem Melching] and [Greg Hogan] got their hands on the power steering (EPS) unit of a Toyota RAV4 Prime, as one of the first cars to implement this new security standard.
As noted by [Willem], the ultimate goal is to be able to run the open source driver assistance system openpilot on these SecOC-enabled cars, which would require either breaking SecOC, or following the official method of ‘rekeying’ the SecOC gateway.
After dumping the firmware of the EPS Renesas RH850/P1M-E MCU via a voltage fault injection, the AES-based encryption routines were identified, but no easy exploits found in the main application. This left the bootloader as the next target.
Ultimately they managed to reverse-engineer the bootloader to determine how the update procedure works, which enabled them to upload shellcode. This script then enabled them to extract the SecOC keys from RAM and send these over the CAN bus. With these keys the path is thus opened to allow any device to generate CAN messages with valid SecOC MACs, effectively breaking encryption. Naturally, there are many caveats with this discovery.
Continue reading “Extracting SecOC Keys From A 2021 Toyota RAV4 Prime”