Sailing the high seas with the wind conjures a romantic notion of grizzled sailors fending off pirates and sea monsters, but until the 1920s, wind-powered vessels were the primary way goods traveled the sea. The meager weather-prediction capabilities of the early 20th Century spelled the end of the sailing ship for most cargo, but cargo ships currently spend half of their operating budget on fuel. Between the costs and growing environmental concerns, [Pierce Nichols] thinks the time may be right for a return to sails.
[Nichols] grew up on a sailing vessel with his parents, and later worked in the aerospace industry designing rockets and aircraft control surfaces. Since sailing is predominantly an exercise in balancing the aerodynamic forces of the sails with the hydrodynamic forces acting on the keel, rudder, and hull of the boat, he’s the perfect man for the job.
While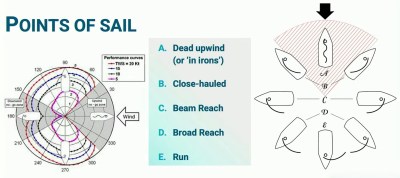 the first sails developed by humans were simple drag devices, sailors eventually developed airfoil sails that allow sailing in directions other than downwind. A polar diagram for a vessel gives you a useful chart of how fast it can go at a given angle to the wind. Sailing directly into the wind is also known as being “in irons” as it doesn’t get you anywhere, but most other angles are viable.
the first sails developed by humans were simple drag devices, sailors eventually developed airfoil sails that allow sailing in directions other than downwind. A polar diagram for a vessel gives you a useful chart of how fast it can go at a given angle to the wind. Sailing directly into the wind is also known as being “in irons” as it doesn’t get you anywhere, but most other angles are viable.
After a late night hackerspace conversation of how it would be cool to circumnavigate the globe with a robotic sailboat, [Nichols] assembled a team to move the project from “wouldn’t it be cool” to reality with the Pathfinder Prototype. Present at the talk, this small catamaran uses two wing sails to provide its primary propulsion. Wing sails, being a solid piece, are easier for computers to control since soft sails often exhibit strange boundary conditions where they stop responding to inputs as expected. Continue reading “Supercon 2023: [Pierce Nichols] Is Teaching Robots To Sail”

















