Some pieces of computing equipment have faded away without a trace, for example a modem is not a device that detains many hackers as they strive for that perfect emulation of a venerable Hayes on an Arduino. But there are some other devices that continue to hold a fascination, even years after they departed from the professional arena. A great example is the serial terminal. Once to be found on many a desk as it provided a way into a minicomputer, it has long ago been supplanted by terminal emulators or simply other portals into computing services such as the web. But in our community there are still plenty of serial terminals to be found, for example [RedHog]’s little emulated VT220 on an ESP8266 platform.
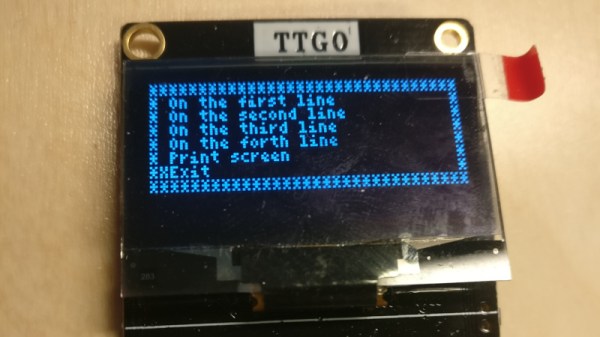
If you were hoping for a full-green screen and keyboard to plug into a hefty D-connector serial port then you’ll be a bit disappointed, as with a tiny screen and only a few buttons on a dev board or an Arduboy it’s not going to allow any 1337 vi mastery even with its on-screen keyboard. Take a look, we’ve placed a video below the break. But despite all that it shows promise, with ability to use either the logic-level serial port or the USB serial interface. We can see that it might find a use as a serial display though, but it would fascinate us to see what could be done were it to use the 8266’s on-board WiFi in some form. If you’d like to experiment you can do so with the code on GitHub.
This isn’t the first such terminal we’ve seen here before of course, some of them have been extremely practical, while others we just want to own because they’re cool.
Continue reading “A Tiny Terminal For Your Serial Access Needs”