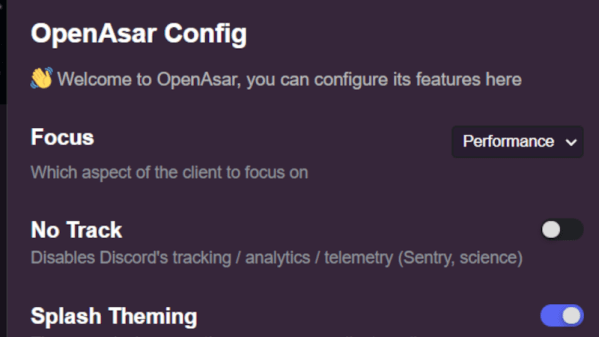
Not all hacking happens on hardware — every now and then, we ought to hack our software-based tools, too. [Ducko] tells us about a partially open-source rewrite of Discord’s Electron-based frontend. Web apps can be hard to tinker with, which is why such projects are to be appreciated. Now, this isn’t a reverse-engineering of Discord’s API or an alternative client per se, but it does offer a hopeful perspective on what the Discord client ought to do for us.
First of all, the client loads noticeably faster, not unlike the famous GTA Online speedup (which was also a user-driven improvement), with channel and server switching made less laggy — and the Linux updater was de-cruft-ified as well. [Ducko] tells us how she got rid of the numerous NPM dependencies of the original code – it turned out that most of the dependencies could be easily replaced with Node.JS native APIs or Linux binaries like unzip. Apart from much-appreciated performance improvements, there are also options like telemetry bypass, and customization mechanisms for your own theming. You won’t get Discord on your Apple ][ just yet, but the native client will be a bit friendlier towards you.
While Discord is ultimately a proprietary platform, we do it see used in cool hacks every now and then, like this tea mug temperature-tracking coaster. Would you like to code your own Discord bot? We wrote a walk-through for that. Last but not least, if you like what we wrote and you happen to also use Discord, you should check out the Hackaday Discord server!